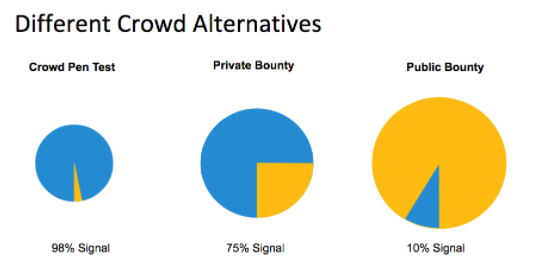
Web application pentesting is the best method of discovering flaws in web applications. Otherwise known as penetration testing or pentest, this process is the leading web application security testing device.
There are various tools for web application pentesting, and the actual pentest is performed using internal and external simulated attacks. These attacks help development teams understand their system vulnerabilities by accessing sensitive data and increasing the team’s awareness of these issues.
Pentests help the end-user to determine security weaknesses in all components of a web application. This includes the database, back-end network, and source code. Using this information, a developer can prioritize any highlighted threats, implementing strategies to mitigate and improve the application.
Why is Web Application Pentesting necessary?
The internet is an essential aspect of many day-to-day tasks. Millions of people use websites and applications to shop, bank, and browse securely. As web applications have become increasingly popular, they are under constant threat from hackers, viruses, and malicious third parties.
As many web applications store or send out sensitive data, the apps must be secure at all times, especially those used by the public.
Web application pentesting works as a preventative control measure, allowing you to analyze every aspect of your web application’s security.
Experts follow a web application pentesting best practices checklist, with overall goals of:
- Test the effectiveness of existing security policies
- Identify unknown vulnerabilities
- Determine the most vulnerable areas for an attack
- Test all publicly exposed application components (routers, firewalls, and DNS)
- Find any loopholes that could be exposed to data theft
Types of Web Pentesting
There are two types of web pentesting: internal and external.
Internal Pentesting
This is a form of manual web application pentesting performed using a LAN from within an organization. During this process, web applications hosted on the intranet undergo testing. Internal pen testing helps to identify any vulnerabilities that exist within a corporate firewall.
Potential attacks that can occur include:
- Attacks on user privileges
- Phishing attacks
- Social engineering attacks
- Malicious attacks from disgruntled employees, contractors, or other parties that wish to harm the business and have access to passwords and security details
Internal pentesting tries to access the LAN without valid credentials and discover the possible malicious attack routes.
External Pentesting
External web pentesting looks for attacks that originate outside of an organization. During this process, ethical hackers are given the target system’s IP address and asked to simulate external attacks. This is the only information they are provided with as they use public data to infiltrate and compromise the target host. External pentesting thoroughly tests an organization’s servers, firewalls, and IDS.
How is Application Pentesting Done?
Following web application pentesting best practices, there are five phases involved in the web application pentesting process:
1. The Reconnaissance Phase
Reconnaissance involves gathering information about your target so that you can plan your attack. This process can be completed actively by interacting directly with the target or passively using intermediaries. Techniques like social engineering and dumpster diving are popular during the reconnaissance phase.
2. The Scanning Phase
Scanning is a more intensive form of intelligence gathering. This process uses technical tools to discover openings in the target listening port, internet gateways, and systems. A vulnerability assessment report is a common practice during this phase.
3. The Exploitation Phase
During this phase, the information discovered in phases one and two is used to infiltrate any target applications and devices. Taking control of these areas allows hackers to access and extract data.
4. Continous Collaboration
Another important step of the pentesting process involves communications between testers and business operators. This empowers the testing process to be more efficient. It also benefits customers whose engineering teams can talk directly with testers to understand discovered vulnerabilities and properly remediate these.
5. Reporting & Remediation
Once a target machine or application has been infiltrated successfully, testers will report back to the customer's engineering teams to relay different vulnerabilities. This process will help kick off the remediation process for the engineers to be able to fix these vulnerabilities.
6. Retesting & Repeat
Lastly, customers using pentesting services should consider retesting their assets after remediation is complete. This will ensure all the different paths to a vulnerability have been properly secured. While not all Ptaas platforms offer complimentary retesting, at Cobalt, this value-add is included with our PtaaS platform.
Furthermore, retesting will be an efficient way to close out a successful pentest engagement. It also helps businesses prepare for future tests as they aim to repeat the process to aim for continued security.
Enhance Your Security with Cobalt
Web applications are convenient and provide a wealth of value to end-users. However, most systems are publicly exposed and vulnerable to attack. Due to increased usage and innovative technologies, web applications are prone to vulnerabilities in configuration and design.
Hackers work hard to identify and exploit these vulnerabilities. Therefore, web application pentesting should be a priority for your business, especially if you store sensitive information.
We provide an easy-to-use pentest as a service (PtaaS) platform with testing performed by professional pentesters. Our clients pay a fixed price based on their testing frequency and application size.
With our Pentest as a Service platform (PtaaS), we simplify security processes and compliance for DevOps-driven teams. Moreover, we can get your pentest implementation ready within 24 hours.
Schedule a demo today and access our focused application security testing solutions. Now is the time to start your pentest program.