In today's digital landscape, one thing remains constant: change.
The digitization of the economy boosted efficiencies but also increased the risks posed by bad actors. Frequent attacks have prompted many organizations to put in place stronger cybersecurity safeguards.
Unsurprisingly, an IBM Cost of a Data Breach Report suggests that the average cost of data breaches has increased by 10%, with the healthcare sector experiencing the most loss over 11 consecutive years. It is no wonder HIPAA compliance has been made mandatory in the health sector.
Today, we have various cybersecurity compliance regulations for many different sectors. Most of the regulations require organizations to undertake a series of security measures to ensure the necessary controls are in place to secure a system. Pentesting is often a requirement or key component to ensuring security compliance.
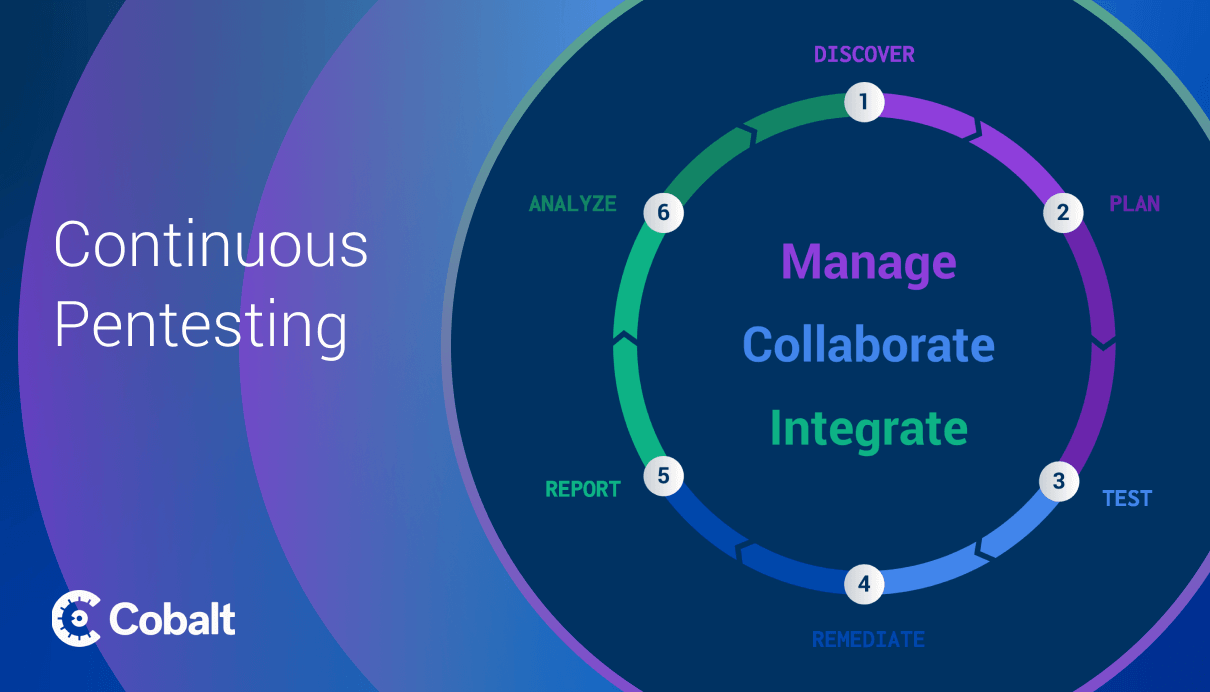
This is why most businesses are now transitioning to a modern approach with continuous pentesting with a Pentest as a Service platform. Continuous testing approaches introduce components such as Agile Pentesting to conduct asset specific or vulnerability specific testing, in addition to Comprehensive Pentesting for Compliance.
If you're a security manager looking to boost your organization's cybersecurity preparedness, keep reading to get a better understanding on continuous penetration testing and its ability to benefit your mission.
What is Continuous Pentesting?
The threat landscape becomes more dynamic with each passing day, making malicious attacks on your IT systems more difficult to prevent. This is worsened by the fact that 82% of respondents to the State of Pentesting 2023 report said they expect their vulnerability backlog to grow this year.
This is where continuous pentesting comes in. Pentesting is meant to simulate real-time attacks on your IT infrastructure so that vulnerabilities can be identified and remediated before a malicious actor exploits them.
Traditionally, pentests would take weeks to months to setup, creating security gaps in the modern software development lifecycle (SDLC). Continuous penetration testing solves this.
Instead of only conducting a couple of these larger pentests throughout the year for compliance, companies can now implement security directly into their SDLC, using services such as Agile Pentesting.
Through continuous pentesting, your organization will have a proactive approach to discovering and dealing with weaknesses that may otherwise go missed.
Agile Pentesting for Development
Agile Pentesting is an approach that enables security testing throughout the development process, mirroring the iterative nature of agile development. It's proactive approach helps mitigate security risks and ensures that security is integral to the development process.
Rather than waiting until the end of the development cycle for a pentest, agile pentesting unlocks security tests in smaller iterations with more focused testing. This enables more continuous feedback cycles between security and development teams to address vulnerabilities early on.
Studies by NIST have revealed that a significant majority of bugs (85%) are introduced during the initial coding phase of development. Fixing these bugs in production can be up to 30 times more costly compared to addressing them during development.
Agile pentesting enables organizations to continuously test during development, starting from the earliest stages and prioritizing the most critical areas in upcoming sprints. Organizations can effectively identify vulnerabilities within the SDLC to applications, web services, and underlying infrastructure by incorporating agile penetration testing.
Agile Pentesting services offer specific testing solutions to enable faster testing, and therefore, faster development. Services range from delta testing to test specific changes in a code base between launch cycles to testing for a specific vulnerability.
Learn more about Agile Pentesting via Cobalt’s innovative PtaaS platform.
How Agile Pentesting Works
In the agile development lifecycle, the first step is breaking down large units of work into smaller, manageable tasks. Unlike traditional waterfall development, where requirements are defined upfront and followed strictly, agile development takes a more repetitious approach.
When paired with Agile Pentesting, agile development starts with a general idea and keeps improving this idea through quick cycles of work, finding and fixing security problems along the way. The iterative approach helps complete development faster and more securely.
Applying this approach to security testing is essential, especially development needs to be conducted swiftly and securely.
Vulnerability Scanners
With continuous pentesting, scanning is another component often used to support a strong security posture. Security professionals utilize scanning technology as a supportive tool to monitor their assets and identify vulnerabilities.
Paired with Comprehensive and Agile Penetration Testing, scanning solutions can be another avenue to identify vulnerabilities quickly for remediation.
The shortfalls of scanning solutions are also something to be aware of. These automatic scanning tools will not catch human logic exploits or other more complex vulnerabilities in your systems. They also generate many false positives that will steal precious time away from security teams despite being nothing more than a distraction.
While security scanners have their place, there are other shortcomings of scanning solutions that become apparent when comparing DAST to Pentesting.
Using Pentesting Beyond Compliance Requirements
As regulations like GDPR, PCI-DSS, or ISO 27001 become more prominent, compliance becomes vital.
However, compliance shouldn't be treated as a mere checklist.
It’s also important to improve your security posture to avoid a costly breach that could impact your bottom line or ruin your reputation with customers.
By leveraging Cobalt's PtaaS model for your penetration testing service needs, you can improve your security posture by identifying vulnerabilities and implementing remediations before a malicious attacker finds them to exploit.