Data security is a high priority across industries. This includes the education sector where confidential files and personal information is stored by school systems and trusted by a vast amount of students, families, and staff to be kept secure. Just as schools value informing students and facilitating learning about topics such as math and history, staying in the know about the topic of cybersecurity plays an important role in maintaining integrity as cyber threats continue to escalate.
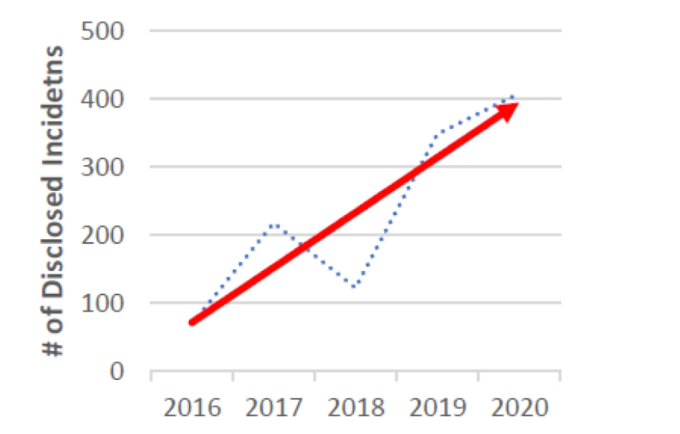
Image from Cyber Attacks on Schools in 2020 Were Record Breaking: Report
As you can see, cyberattacks on schools are on the rise and are projected to continue to trend in this direction. “IT leaders must first recognize that for the foreseeable future, the complexity of software and systems will only multiply. Adding to the struggle is the volume and variety of these tools, as they shift from managing some operating systems, apps and devices to having to manage so much more. Moreover, many schools lack the bandwidth and resources to be properly prepared for a cyber security incident.” (Cyber security threats to schools and how to protect against them)
It’s important for educational institutions to ask themselves questions such as: What information is safe to share online? What do you do if an attack or a data breach occurs? Is your staff trained on best practices for detecting and reporting suspicious activity? What security plan can you set in place for the future?
Top 5 Cybersecurity Risks for Schools
1. Phishing
Phishing attackers falsify legitimate-looking emails in an attempt to compromise personal information through an email open or click.
What can you do to prevent falling victim to a phishing scam?
Stay away from suspicious-looking emails from unknown senders, and avoid clicking on links that can lead to accidentally sharing passwords, credit card information, phone numbers, and more. Installing an anti-phishing toolbar and using anti-phishing software are additional security controls to help avoid attacks.
2. Distributed Denial-of-Service (DDoS)
DDoS takes advantage of vulnerabilities and weaknesses in devices by manipulating and turning devices into bots and forcing them to send multiple requests at the same time to a network or server's IP address. When so many simultaneous requests occur, the network/server will crash and be unable to deliver its basic functions. When a server is unable to respond, this can result in students not being able to access resources, upload assignments, etc. Elevating security settings, planning ahead to avoid exploitations, and implementing a DoS protection service are all ways to avoid the severity of a DDoS attack.
3. Data Breaches
Sharing personal information online creates a variety of risks. Schools, in particular, run the risk of releasing confidential information in an unanticipated data breach. Data breaches occur when information is compromised and stolen from a system without authorization. Keeping security software up to date, fully securing computers, and safeguarding data helps to prevent these types of unwarranted attacks. Other security controls include encryption, firewalls, and vulnerability monitoring & management.
4. Ransomware
Ransomware is a type of malicious software used by cybercriminals to encrypt files on devices and deny access to the rightful owner, leading to an ultimatum of a “ransom” payment to retrieve access. Ransomware can lead to severe data and/or financial loss for institutions. With a recent increase in schools reporting ransomware incidents, it’s important to have policies in place to prevent ransomware attacks. Further developing a cybersecurity maturity model helps to alleviate some risks associated with ransomware.
5. IoT Vulnerabilities
IoT (Internet of Things) devices transmit data wirelessly through a network. These devices include security cameras, laptops, desktops, and tablets, many of which are typically found in classrooms and widely used by schools to enhance learning in the increasingly digital world. Making sure to update software frequently and implement end-to-end encryption is key to preventing attackers from exploiting IoT vulnerabilities and compromising sensitive information. IoT and device testing helps companies secure physical equipment and avoid the costs associated with cyber attacks.
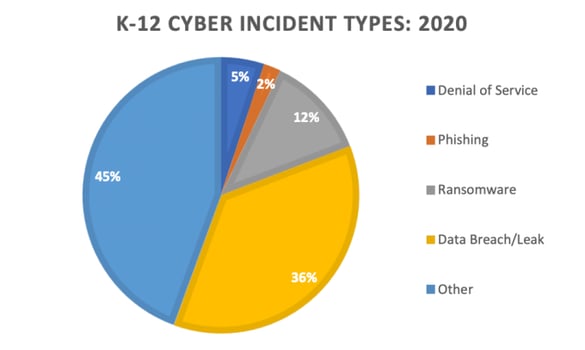
Image from The State of K-12 Cybersecurity 2020 Year in Review
There are various types of cyber incidents that can pose risks for schools. Sound cybersecurity habits such as continuous pentesting, implementing security scanners, regularly updating software, and promoting security awareness and education are all ways to protect against different types of potential cyber attacks. It’s essential to create a space in educational institutions where teachers and staff, as well as students, are informed about the importance of cybersecurity.
As Caroline Wong, Cobalt’s Chief Strategy Officer, said in Kids Are Curious About Cybersecurity — Let's Teach Them: “Kids are often smarter and far more observant than we give them credit for. They may notice and think about cybersecurity issues that would never cross our minds. Create space for them to voice their own worries about the internet and cybersecurity. You might be surprised by what they know.”
Parents, teachers, and students have all had to navigate the risks of cybercrime with both in-person and online learning. Focusing on lessons to draw from previous years is key to planning ahead to maintain a safe and secure learning environment. Furthermore, threat modeling offers educational institutions an efficient way to better understand their unique cybersecurity risks and mitigate them accordingly.
Partnering with a Pentest as a Service (PtaaS) platform makes securing data easy — get started with Cobalt today to mature your security program through a scalable, data-driven approach to pentesting with real-time insights and a plan for remediation.









