*Azure ID was rebranded to Microsoft Entra ID in 2023.
What is Azure AD?
Most corporate companies have to use Microsoft Active Directory to manage their domain environments because there is no alternative. Corporate companies with thousands of employees need to operate through a single management panel. It is essential to define which employees of the companies have authority over which system or group. Identity and Access Management (IAM) is the IAM service.
Active Directory has been used for a long time in on-prem systems. The prevalence of Microsoft Windows operating systems and the use of Active Directory has become almost a necessity for corporate companies. It has made it necessary to meet Azure AD for companies that want to use cloud technology. After developing cloud technologies in recent years, Microsoft Azure AD has opened the IAM service in cloud technologies. We already know the popular attack methods on On-Prem Active Directory. This article will get to know Azure AD technology, learn the attack surface, and learn the tools used in penetration testing.
You can learn the differences between on-prem Active Directory and Azure AD from the site below.
Compare Active Directory to Azure Active Directory
Why does Azure need to pentest?
Due to the prevalence of Azure AD Active Directory usage, corporate companies widely use it. As it is a hybrid technology, there are access control risks such as On-Prem to Cloud and On-Cloud to On-Prem. It is possible to access the on-prem Active Directory controller through a compromised system on the cloud, and it is also possible to log in to Azure AD via the on-prem Windows systems. Attackers can also exploit a detected vulnerability in web applications on Azure, and your on-prem or on-cloud active directory infrastructure can be exploited.
Considering these risks, I strongly recommend that you include Azure AD in penetration testing, whether you have an internal or external network structure.
Azure AD Attack Surface
External Network
If you have a web, mobile, API application on Azure or use Blob Storage, you could potentially be a target of cyberattacks.
Most Azure Web Services applications run with Managed Identity permissions. Due to the vulnerabilities in the web application, the on-prem AD environment may become a target if the attacker captures the access token belonging to this user.
Any corporate user on Azure AD may be the victim of a phishing attack, and a cyber attacker may steal your user's access token. With these user rights, cyber-attacker could gain persistence on Azure AD.
If you are using Storage or Function Apps services, you need to ensure that you have them configured well enough.
Internal Network (Resources & APIs)
It is imperative to test your penetration test with different user profiles (anonymous, company employee, customer, etc.). If you are using Azure AD, you need to determine the rights of your corporate employees and their authority on Azure AD. One of your on-prem Active Directory users may have access to your cloud resources, or you might not know that one of your cloud users may control the on-prem Active Directory. Conversely, a user or service account in the cloud environment can perform unauthorized transactions in your on-premise domain environment.
Azure AD: Reconnaissance
You only know the company's domain name that you will perform the penetration test for, for example, Contoso.com; based on this information, we can obtain some helpful information. These are listed below;
- Tenant ID
- Tenant Name
- Domains
- Azure services (used by the organization)
- Email IDs
- Valid/invalid Users
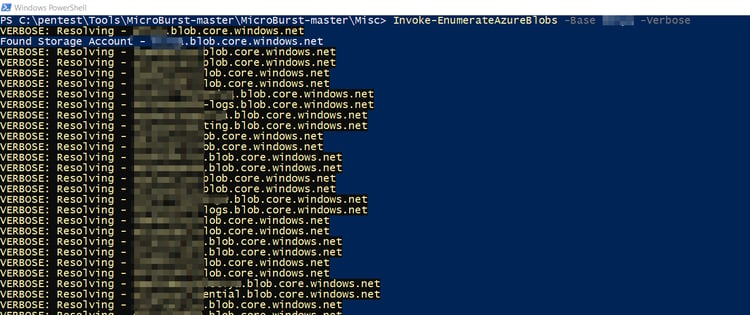
- Public Azure Blobs
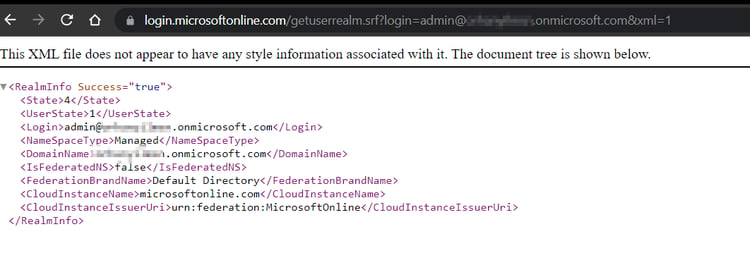
Tenant Name
Tenant represents an organization in Azure Active Directory, an instance ID. You can query the user's login information and tenant name on the following endpoint.
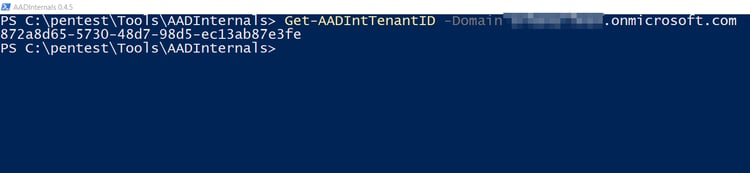
Tenant ID
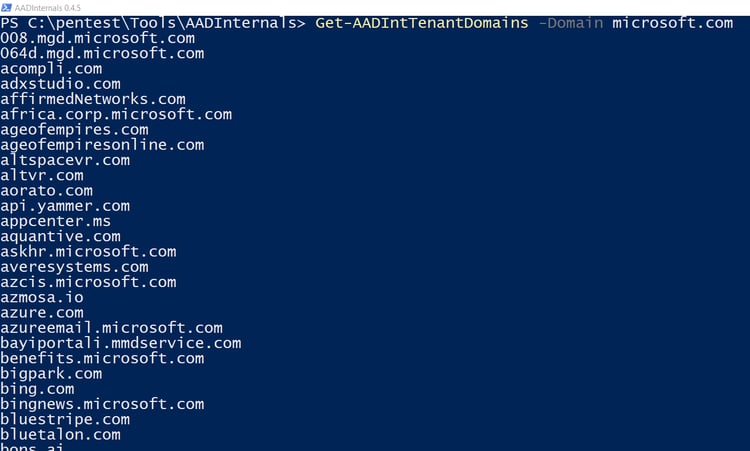
Domains
We can use the following commands to detect the domain's subdomains on Azure.
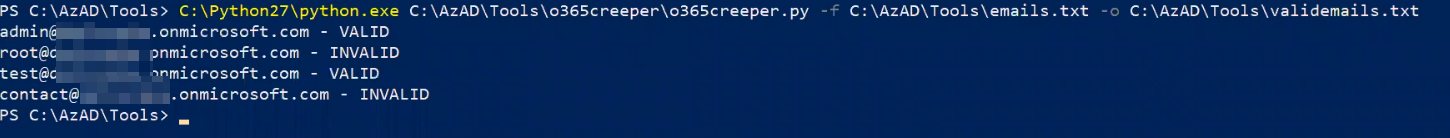
Email IDs
Azure services
You must check the accessibility of which Azure AD users are using services. Depending on the determination of who can use services and memberships, you can create different attack surfaces.
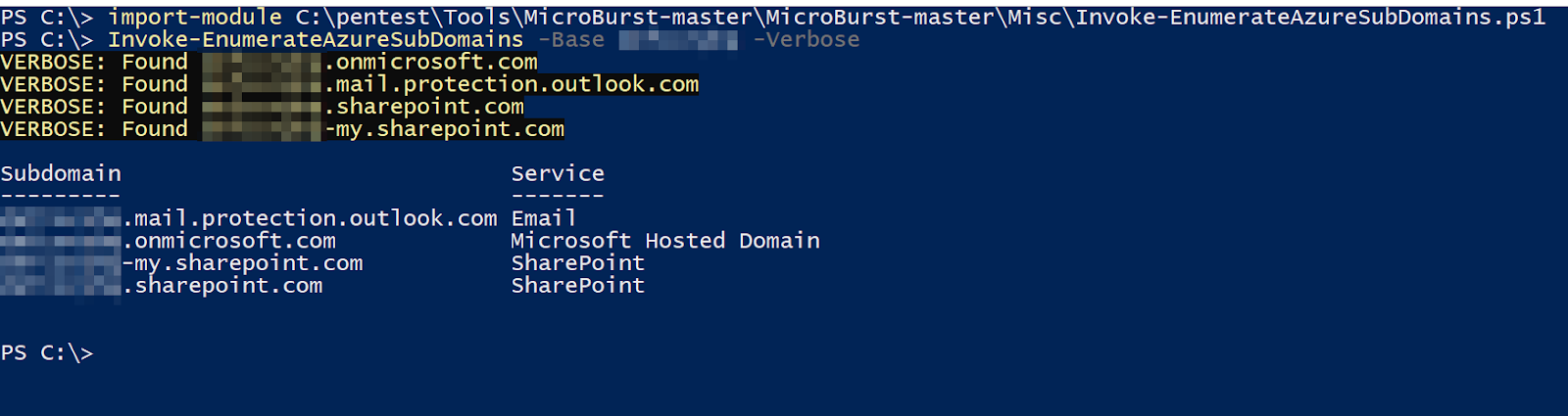
Public Azure Blobs
This tool can detect publicly accessible Azure Blogs. Afterward, it can connect to the store, and enumeration allows anyone to see confidential information.
Azure AD: Initial Access
Accessing the Azure AD environment can be achieved in many ways. The main ones of them are below.
- Password Spraying / Brute Force Attack
- Phishing Attacks
- Web Application Vulnerabilities
- Illicit Consent Grant Attack
- Function Apps
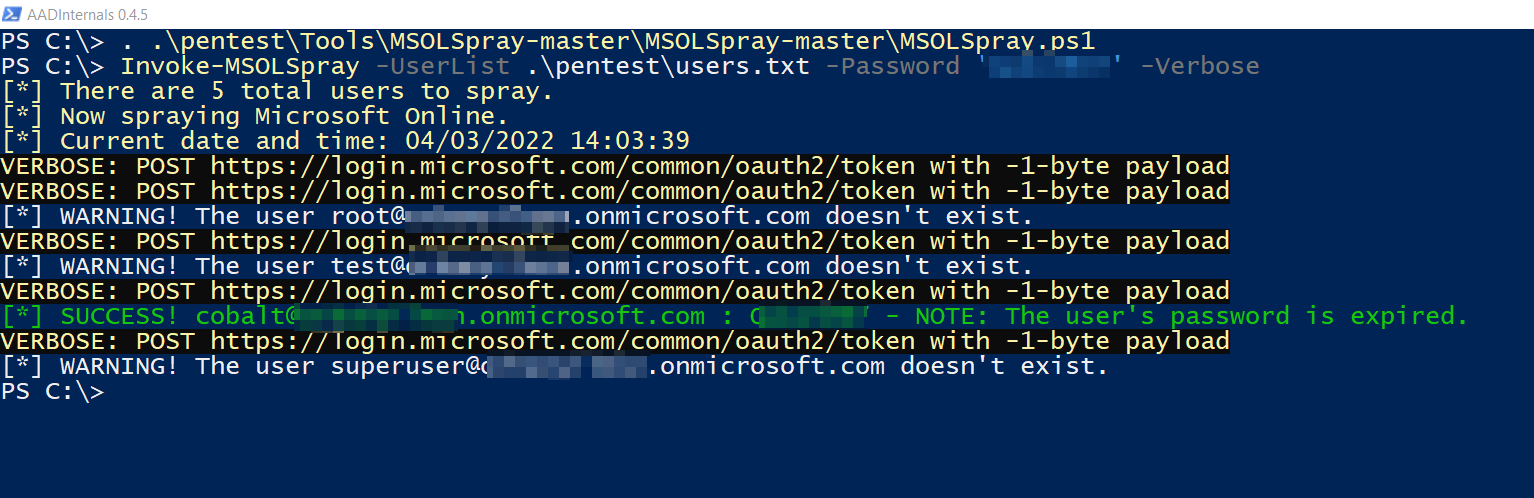
Password Spraying
There is a tool called MSOLSpray, which is very capable. With this tool, we can obtain the following information.
- User Validation
- MFA Status
- Tenant Exists
- Disabled/Locked Account
- Password Expired
Web Application Vulnerabilities
Your web applications on Azure can run with Azure Function Service or Azure App service permission, such as managed identity. If these applications are running with Managed Identity rights, they can gain unauthorized access to Azure Resources if the cyber attacker captures the access token belonging to this user. Suppose a command execution vulnerability is detected on your web applications. In that case, it can be determined that the application is running with Managed Identity rights, whether the following two variables are defined over the environment.
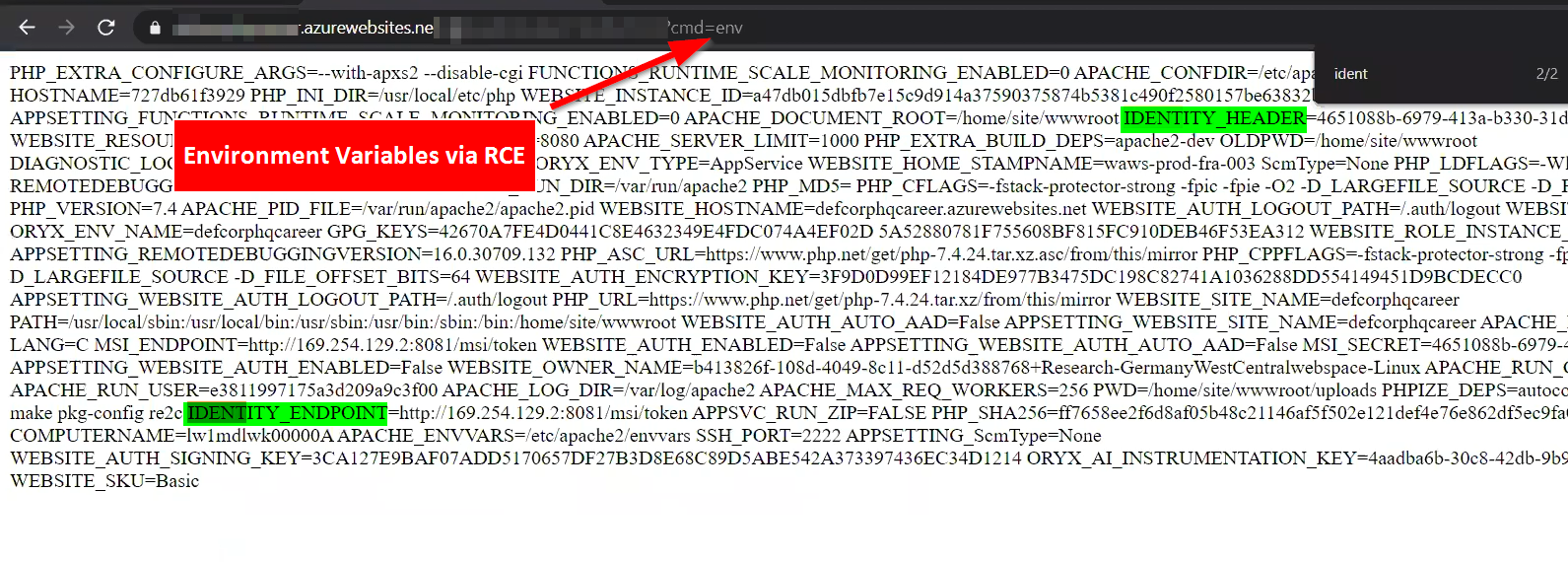
After an Azure web service application with remote code execution is detected, the Azure Resource Manager (ARM) endpoint is triggered to obtain an access token with Managed Identity rights. You can get access tokens through the following endpoint.
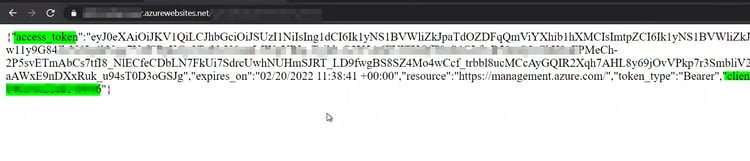
With this informations, authenticated enumeration can now be performed on Azure AD using the Az PowerShell tool.
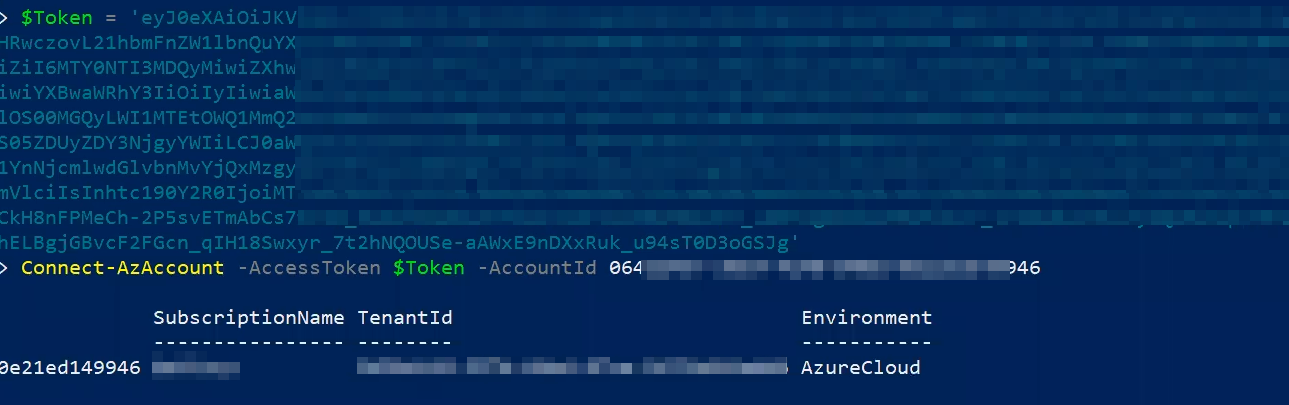
After authenticating to the Azure AD environment with Managed Identity, you can access Azure resources with the following command.
Phishing Attacks
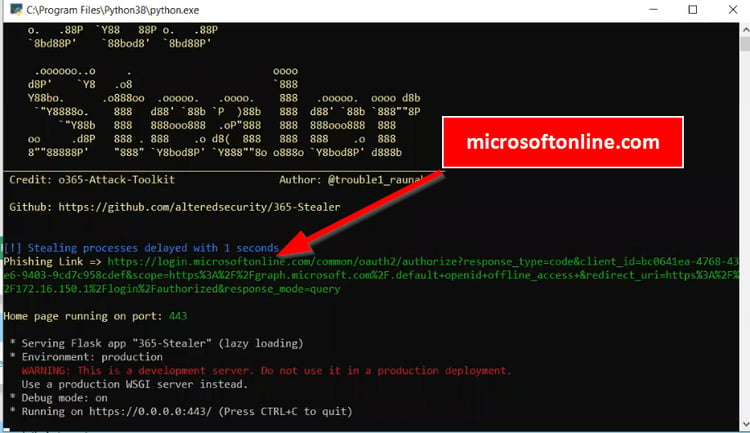
A phishing link can be created with the OpenRedirect vulnerability created using the 365 stealer tool Microsoft domain. By sending this phishing link to Azure AD users, you can obtain the access token information of the user.

The phishing link created using this tool is very dangerous as it is microsoftonline.com. The related tool sends the access token information of the user to the cyber attacker by POST method. The cyber attacker captures the token information of the user.
Azure AD: Enumeration
After gaining access to Azure AD belonging to the target organization, the first goal is information gathering and enumeration. The following tools can be used to do this on Azure AD.
- StormSpotter
- BloodHound
- ROADTools
- Authentication via CLI (Az CLI, Az PowerShell, AzureAD)
Enumeration with Az PowerShell
User Enumeration
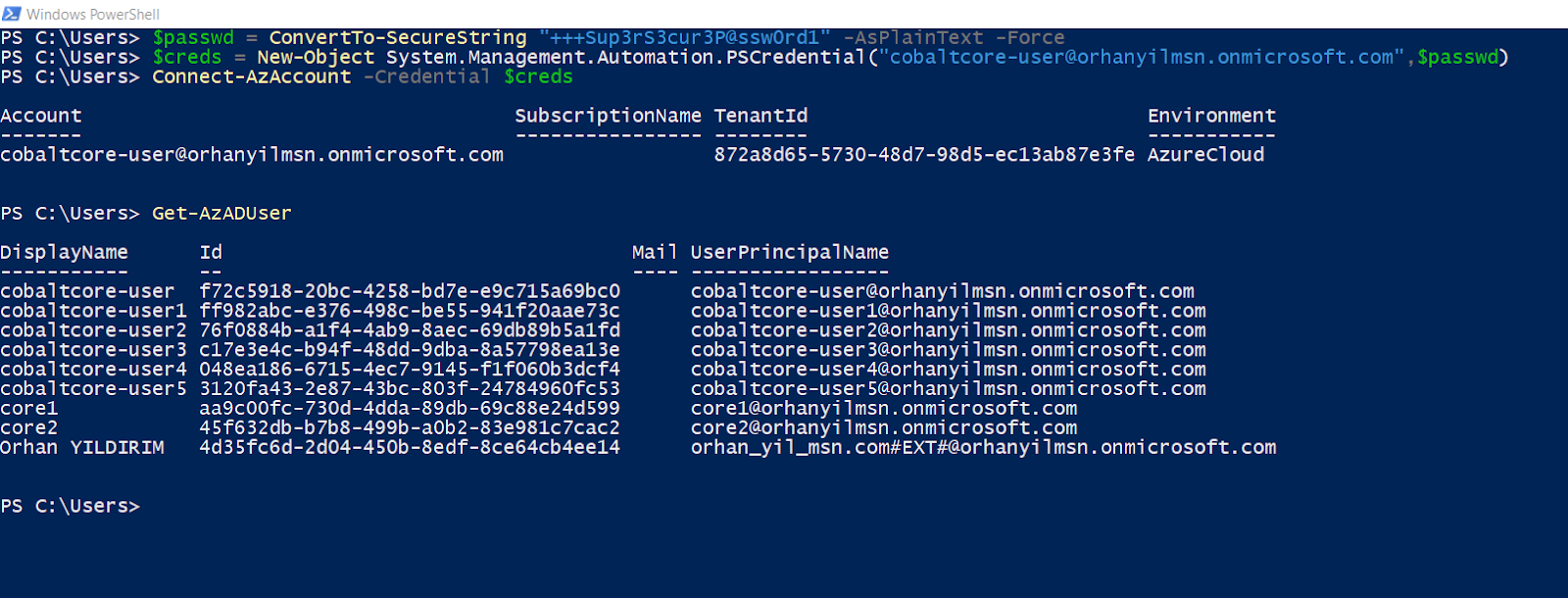
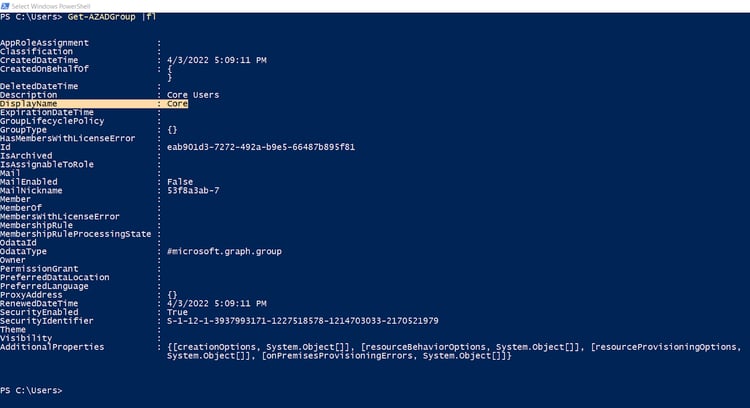
Group Enumeration
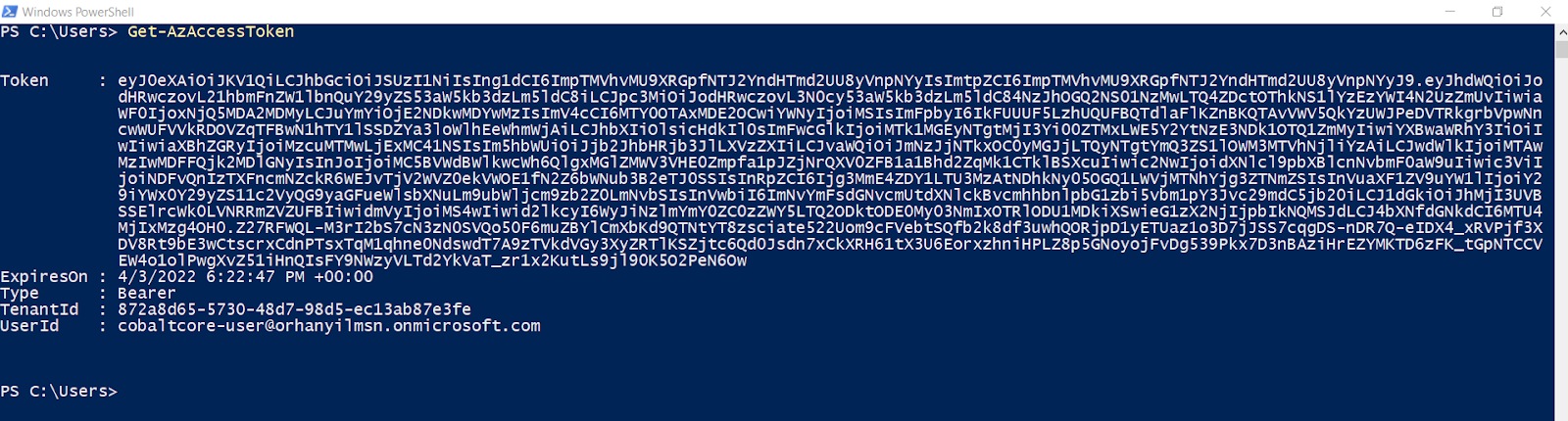
Get A New Access Token
Azure AD: Lateral Movement
After obtaining first access to Azure AD, the next goal for the cyber attacker is the attacks we call lateral movement. At this stage, the cyber attacker tries to access different resources on Azure AD with the access token information of the user it has accessed and aims to capture the access token information of a more authorized user. There are many different control steps for this.
- Azure Resources
- Role Assignment
- Runbook
- PowerShell History
- Automation Account
- ARM Templates
- User Data
- Custom Script Extension
- Azure VMs (Hybrid Joined)
- Primary Refresh Token (PRT)
We will review a few of these titles.
Azure Resources & Runbook
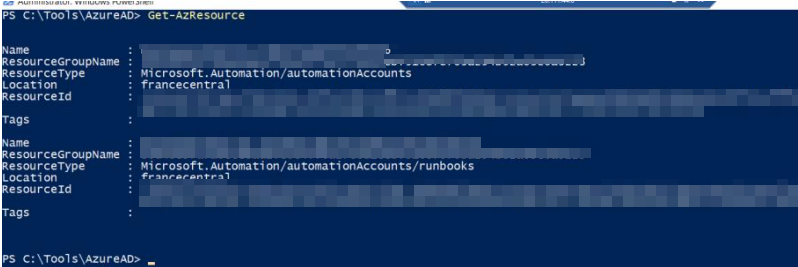
In the Initial Access part, we obtain the access token information of a user with managed identity rights over the web application. We are authenticated to the Azure AD environment using the Az PowerShell tool with the token information we obtained. Then we check which Azure Resources the user we received can access.
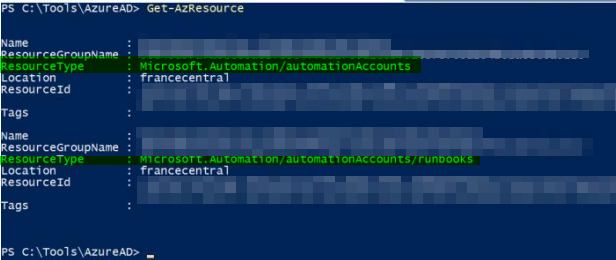
As seen in the screenshot, we have permission on Automation Accounts with the access token information that we have access to. Now we can access the password information of the admin or users with different privileges on the existing Runbook scripts (PowerShell, Python, etc.). With the necessary permissions on the Automation Accounts service, we have the required permission to export, import, publish, and start the existing Runbook scripts!
In this way, the cyber attacker can run a malicious PowerShell script and obtain initial access to this system, mainly if Hybrid Worker is defined on Azure AD and can obtain a session on a pre-premium system from the Cloud structure.
PowerShell History
If you are a system administrator and operating on Azure AD using the PowerShell terminal, you should make sure that you terminate your session safely. System administrators perform operations on Azure AD using the following tools with a PowerShell session.
- Az PowerShell
- Az CLI
A user who has an access token can perform operations on Azure AD using the following way.
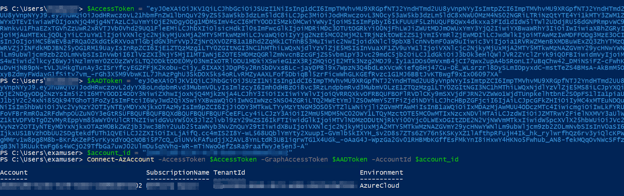
Az PowerShell keeps the user's session information authenticated in the TokenCache.dat file on C: ⁇ Users ⁇ [username] ⁇ Azure. Access token information is kept as clear text in this file path. You must finish the Azure AD session with the Disconnect-AzAccount command.
When using the Az CLI tool, the access token information is available as clear text in the accessTokens.json file on the C:\Users\[username]\.Azure file path. To bypass this, you must terminate the relevant session with az logout command.
If you do not log off properly after using these tools, access token information will be obtained by cyber attackers.
Azure AD: Persistence
A cyber attacker who gained an authorized user account with lateral movement attacks on Azure AD can use different techniques to gain access to Azure AD.
- AZUREADASSOC
- Federation - Trusted Domain
- Storage Account Access Keys
- Applications and Service Principals
This title will examine the Applications and Service Principals technique, one of the persistence techniques. In this method, when we obtain the user privileges with Global Administrator rights on Azure AD, we must create an application with high privileges. With the application we made, we can create an application with password reset privileges on the Global Administrator user.
Resources








