At Mobile World Congress in 2019, Microsoft CEO Satya Nadella said that with the state of the world, every company is now a software company, meaning computing is a core part of every industry. Take the automotive industry, for example: A car is now a computer. So how can companies differentiate themselves when we’re moving towards a world where these demarcations may disappear? Gunter Ollmann, CSO of Microsoft’s Cloud and AI Security Division, says that to be successful, you must differentiate yourself by mastering the software of your company and developing code that is both functional and secure.
Ollmann has more than 30 years of experience in the security industry. He has trail-blazed new security markets, invented revolutionary classes of technology, built and led globally recognized research teams, and has provided expert counsel to Fortune 100 companies for decades. When it comes to software security, he is highly-regarded as one of the world’s most reputable experts.
We were honored to have Ollmann give the keynote at our recent Shift Appsec Summit, where he explored the state of secure software, taking a look at where we’ve been, where we stand today, and what we can expect to see in the future. Here’s a summary of what he shared.
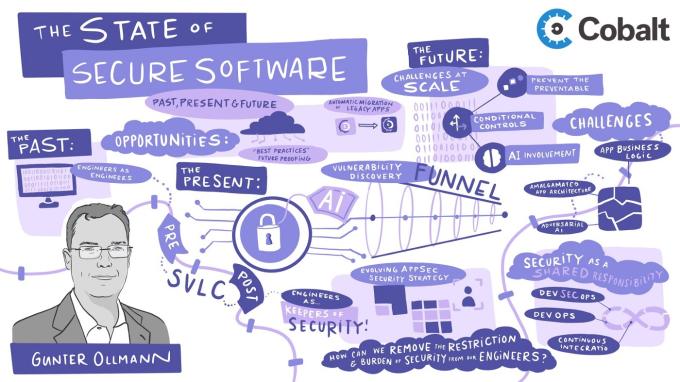
The Past: A Movement to Streamline Development
The first secure development milestone was the creation and implementation of the Secure Development Lifecycle (SDLC) ‘watershed’.
Before SDLC, engineers were incentivized to ship projects fast. This was characterized by:
-
Wild west coding practices.
-
“Security engineers” reserved for high-value code only.
-
A “don’t break the build” mentality.
-
The view that security issues were ‘bugs’ that could be fixed post-release.
After SDLC, things changed. Security became accepted as a necessary part of the development process:
-
Training, awareness, and best practice became the norm.
-
Every engineer became a security engineer.
-
Code was routinely checked for known security issues.
-
Security testing became part of the build process.
At its core, this cycle brought a consistent methodology and a clearly-defined process to the software world. It set a standard for developing, altering, maintaining, and replacing software at speed and brought security into the overall software process.
The Present: Scaling Secure Development in the Cloud
Right now, we’re seeing a “shift left” in secure development, where code is being tested earlier in the SDLC. At the same time, the move to the cloud is changing dynamics of how organizations must create, adapt, secure, and operationalize code.
For cloud software to be secure, engineers must be proactive in identifying and removing vulnerabilities as early as possible. To facilitate this, there have been three major adjustments:
-
Continuous Integration, Continuous Delivery (CI/CD) — an effort to build security into the development lifecycle.
-
DevOps — the nuts and bolts of CI/CD in practice, including how humans and automation combine to deliver secure software.
-
DevSecOps — integrating security as a shared responsibility.
To bring this to life, Ollmann shared an example from Microsoft, who as we all know, ships a ton of code. To ensure shipped code is resilient, they use what is called the Vulnerability Discovery Funnel. Let’s take a look at what that funnel includes:
-
Static analysis to find and remove obvious security flaws.
-
Scalable fuzzing of source and compiled code using automated tools.
-
Attack surface analysis to identify the entry points and threats most likely to affect a piece of code.
-
Dynamic sanitization of code using automated tools to find coding issues that aren’t necessarily security flaws.
-
Pentesting using automated and human processes to identify vulnerabilities that a human might find.
-
Red team exercises to determine how secure the code and application are in a real-world context.
This amount of testing requires so much effort that even if Microsoft hired every pentester on the planet, there’s no way every piece of code could be inspected. This casts light on an issue that will become increasingly widespread as companies ship more and more code, and a shift in approach is necessary in order to keep up with developer output and effectively secure code at scale.
Ollmann identified three areas for immediate improvement:
-
At the point of code creation, it should be hard for developers to make errors. Coding issues should be automatically identified and corrected.
-
Static analysis functions need to run early in the SLDC with a low false-positive rate. These functions must highlight critical issues and give actionable advice.
-
Fuzzing technologies need to be easy-to-use and productive — an automatic ‘pen test’ that can check every line of code before it’s shipped.
The Future: Exploring AppSec Opportunities
In closing, Ollmann identified the biggest security opportunities that will help resolve these challenges. He categorized these opportunities as near, mid-term, and long-term billion-dollar opportunities.
Near Term Opportunities:
-
Prevent the preventable — Create secure coding languages and libraries and enable drag and drop service development.
-
Conditional controls — Enable seamless integration with native platform security apparatus to reduce the onus on the user.
-
AI involvement — Embed AI assistance throughout the DevOps cycle to automatically identify and correct security issues in code.
Mid-Term Opportunities:
-
Application business logic — Uncover and preemptively fix flaws in application business logic, particularly in public cloud infrastructures where customers bring their own code.
-
Amalgamated app architectures — Detect logic and connector flaws in massive, multi-environment distributed applications with a mixture of old and new code, and even different code infrastructures.
-
Adversarial AI — Defend against fully-automated and AI-based attack systems that find bugs and create exploits faster than a human can patch.
Long-Term Multi-Billion-Dollar Opportunities:
-
“Best practices” future-proofing — Applications need to intelligently and automatically adopt and enforce best practices without future developer involvement.
-
Automatic migration of legacy apps — There needs to be a way for legacy application code to be intelligently transformed into cloud-native code that incorporates best security workload practices.
Ollmann believes that if you seize the opportunities described above (especially the last two), organizations around the world will line up to write billion-dollar checks. Of course, many organizations are actively working on solutions to these problems, but we need to help keep them focused on real solutions, not just buzzwords. We have the ability to drive change and true innovation in the industry. It’s up to us as security leaders and practitioners to learn from our past and understand the specific challenges we currently face to create a better future.









