Pentesting for compliance simply isn’t enough.
For the past five years, the State of Pentesting 2022 Report has shown companies are dealing with the same top 5 vulnerabilities year after year. In other words, the modern agile software development life cycle (SDLC) requires more than pentesting for compliance.
Industry statistics show that nearly ⅔ of companies use agile development methodologies. Thus, it makes sense to also implement an agile approach for testing to ensure new product launches, features, or other changes to your code don't launch alongside vulnerabilities.
With that in mind, let’s take a look at an example timeline for companies looking to take their security program to the next level. This will include standard compliance testing but also ancillary services such as red teaming and also leaner testing services such as what’s offered by Cobalt’s Agile Pentesting services.
Pentesting Program for Compliance isn’t Enough
While pentesting to meet compliance requirements such as required by SOC 2, PCI, or many other standards is a great start – it’s simply not enough. Companies today require a more targeted approach for their security testing to align with the continuous software development lifecycle.
To start, companies using an agile SDLC will often release many smaller changes to their products which could introduce new vulnerabilities. Furthermore, in the dynamic world of cybersecurity, novel exploits such as Log4J can disrupt a secure environment. To solve for this, companies should consider taking a more iterative approach with their pentesting programs.
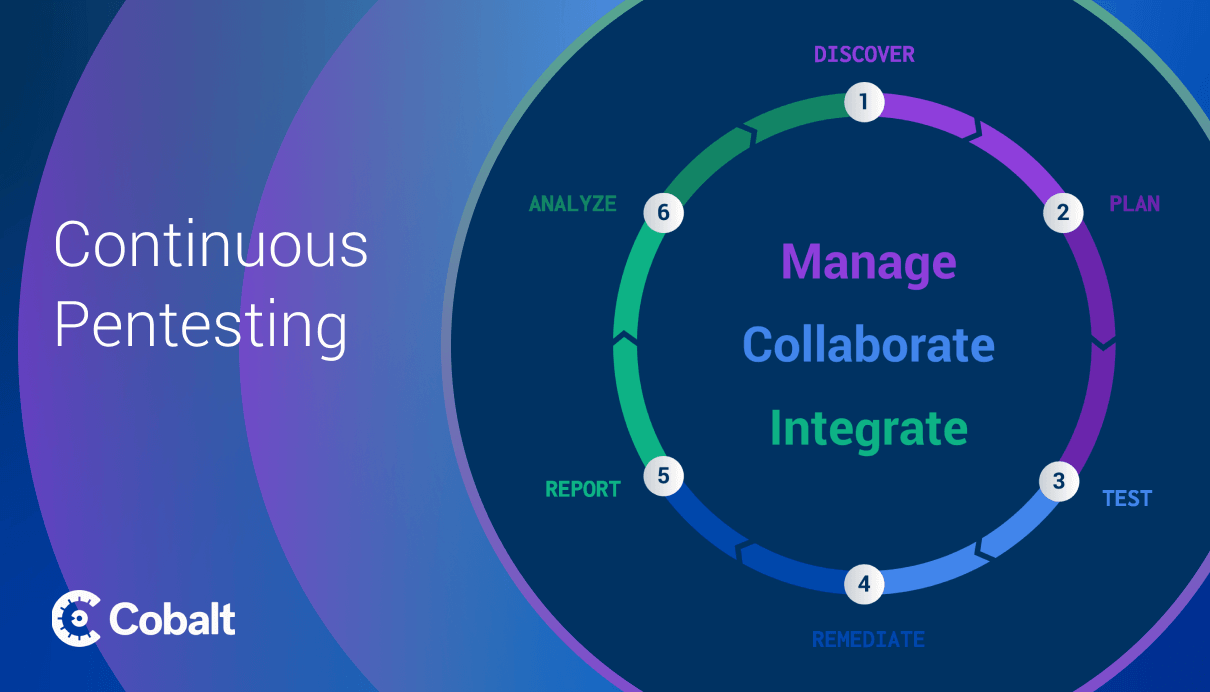
At Cobalt, we realize a pentest is for a single moment in time. Yet, the real world is constantly changing. That’s why we visualize the pentesting process as a lifecycle. This framework provides an easier way to see the testing process as on-going. Also, it starts to illuminate the benefits of conducting pentests using a platform (such as Cobalt’s Pentest as a Service (PtaaS) platform *wink* *wink*)
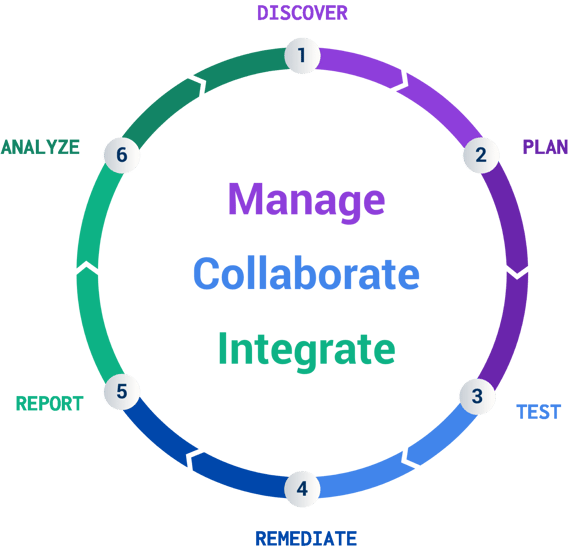
Other benefits from utilizing a PtaaS platform for your pentest program include:
- systematic learnings
- free retesting after remediation (on Cobalt’s platform)
- increased collaboration between developers and security professionals
Let’s take a closer look at each of these benefits.
For a pentest program to unlock its full potential, companies should be gaining knowledge through each test and identifying systematic ways to improve security so vulnerabilities aren’t repeated.
For example, a new feature may require new developer tasks and unknowingly introduce the same category of vulnerability to a codebase. With a view beyond a single pentest, companies can learn about this trend from their historic pentest reports and start to fix the problem before it’s even created by changing the particular process commonly introducing the vulnerability.
Another important value proposition for companies using a PtaaS platform comes from the free retesting offered by Cobalt.
Not only does the free retest allow developers to ensure remediation properly removes a vulnerability, it also allows developers to see their work from the perspective of a security professional. We shouldn’t expect developers to know how to do pentesting. Instead, increased communication between pentesters and developers will empower development teams to better understand the root cause of security vulnerabilities and hopefully avoid the same vulnerability during future projects.
Lastly, a pentest program built using a PtaaS platform increases remediation efficiency by remediating different attack vectors for the same vulnerability. The increased communication paired with retesting unlocks this final value add. Also, as our pentesters are in constant communication with your team, you can begin to fix the vulnerability as soon as it’s discovered. No need to wait for the end of the pentest engagement. As noted above, this can increase the security of a company, while also enabling developers to learn security best practices.
To keep pace with the agile development process, it requires a new approach to pentesting. Cobalt’s answer to this is Agile Pentesting.
SDLC Pentesting for Agile Teams
To help companies execute a stronger pentest plan that’s more proactive, Cobalt’s introduced new Agile Pentesting Services. These include a variety of different targeted pentesting use cases including:
- New Release Testing
- Delta Testing
- Exploitable Vulnerability Testing
- Single OWASP Category Testing
- Microservice Testing
With these more specific types of pentests available, Cobalt empowers companies to conduct pentesting strategically.
Although not often thought of in this light, a pentest can certainly be strategic to support security operations with a faster cadence of testing — similar to changes to the development process such as with agile SDLC.
That being said, pentesting alone is only one component to a broader security plan. Other activities such as code review, red teaming services, or phishing engagements — all aim to increase a company’s security posture and should be considered by businesses to do so. If you need help with any of these security services, check out Cobalt’s professional services.
Example Pentesting Timeline
As cyberattacks increase each year, it's important companies start to consider pentesting beyond a compliance checkbox.
Here’s an example of a security program overview that's now enhanced with Agile Pentesting and other supplementary professional services.
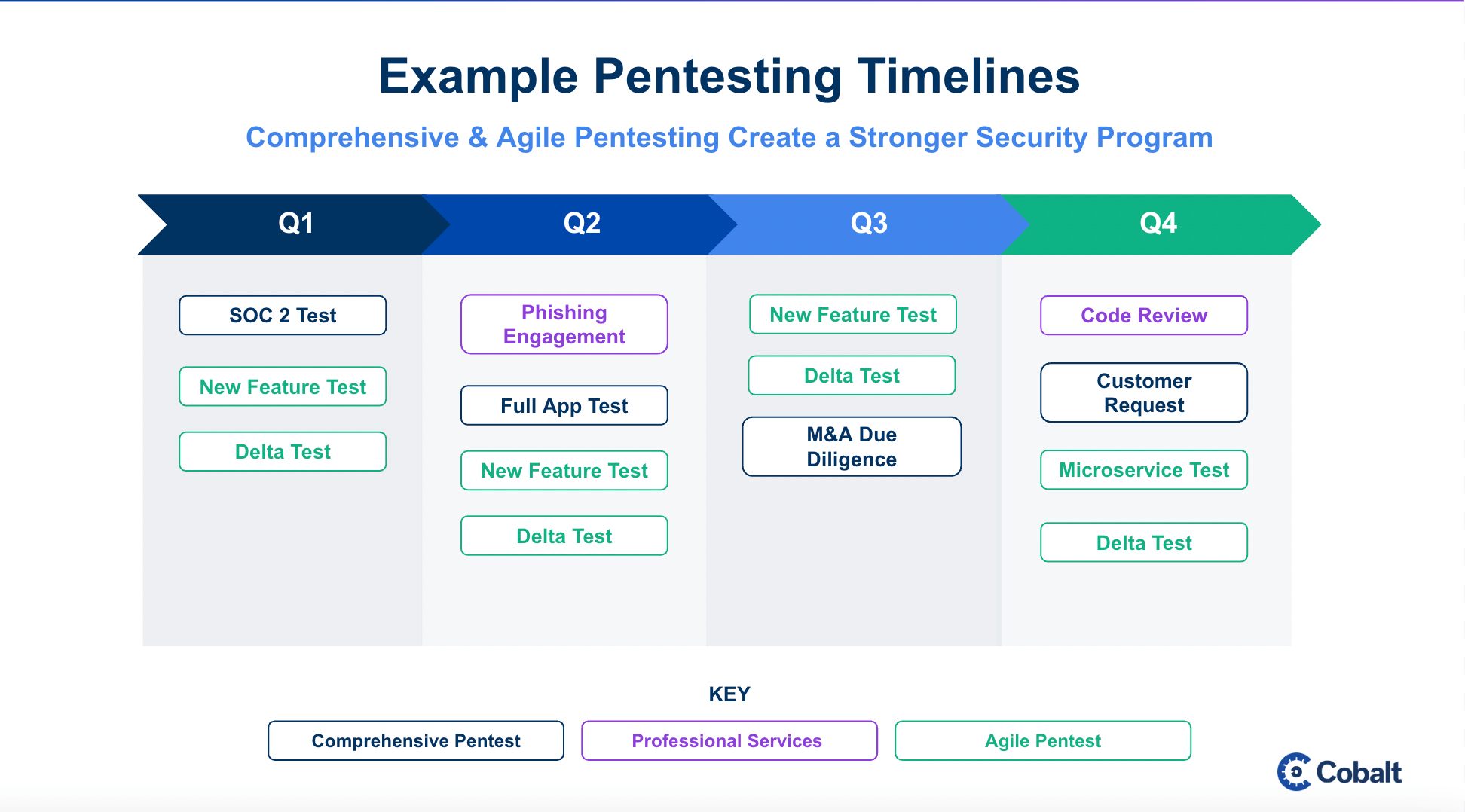
In this more rigorous testing timeline, companies benefit from both Agile and Comprehensive pentests; while also leveraging professional services such as a phishing engagement or code review service to increase their security coverage.
With today’s dynamic threats and fast development life cycles, these extra security measures should be considered by any firm looking to have a strong security posture.
Conclusion
Remember there’s more to a pentest than the test itself.
While increased security coverage is the main benefit of a pentest, there’s many others to discover. For example, a strong pentest program empowers developers to learn security best practices and companies to learn from their past tests to improve future processes.
Lastly, remember a strong security program includes both Comprehensive Pentests for compliance in addition to Agile Pentests and other professional cybersecurity services. See how Cobalt's platform empowers your pentesting to be more efficient.