If you’ve read security blogs or attended conferences in the last few years, you’ll have already heard the term plenty of times.
Your organization may even have an active threat intelligence program.
For many people in the industry, though, it’s still not clear how threat intelligence can help build an effective security program. In fact, many security professionals believe that threat intelligence programs are a waste of time and resources. We disagree with this — but only if threat intelligence is applied properly.
In this article, we’ll explain what threat intelligence is, how it relates to pentesting, and how it can help your organization prepare for real-world threats.
What is Threat Intelligence?
Before we get into the specifics of threat influence led pentesting, it’s important that you understand exactly what threat intelligence is. Gartner defines it like this:
“Threat intelligence is evidence-based knowledge, including context, mechanisms, indicators, implications and actionable advice, about an existing or emerging menace or hazard to assets that can be used to inform decisions regarding the subject’s response to that menace or hazard.”
Simply, threat intelligence is about understanding the threats faced by your organization. Ideally, that includes:
-
Who is likely to attack you
-
What they are likely to target
-
When attacks are likely to occur
-
How they are likely to carry out the attack
Notice the word ‘likely’ in each of the above bullets. Threat intelligence is not a guarantee. It’s a way to measure the cyber risk associated with different assets, attack vectors, and threat actors. If you have access to a strong threat intelligence asset, defining and incrementally improving your security program becomes much more manageable.
Of course, not all of the intelligence listed above is available at all times or to all organizations. Most of the time, threat intelligence provides a partial picture of an organization’s threat landscape. The rest of the picture must be built up using internal knowledge, industry best practices, and assessments based on appropriate security and compliance frameworks.
Equally, threat intelligence is — by its very nature — based on past and current events. For obvious reasons, these aren’t always a perfect predictor of the future. A strong threat intelligence program can help an organization build an effective, risk-based security program, but can’t guarantee protection against genuinely new threats.
With all of that said, threat intelligence is a highly-effective means of determining cyber risk. Equally, the information it provides can inform a wide range of preventative and proactive security measures.
Good vs. Bad Threat Intelligence
The single most important thing to understand about threat intelligence is that it’s only valuable if it informs action. There is ZERO VALUE to threat intelligence if it can’t be directly actioned. And critically, threat intelligence can only be considered actionable if it’s tailored to your specific organization — that means your environment, your security program, your industry, and your threats.
Unfortunately, bad threat intelligence is everywhere. Much of the content from free threat feeds and industry news sites is interesting but not actionable. This type of intelligence can be a huge time sink if you aren’t careful. Just as many organizations find themselves reacting to the latest security headlines, you’ll quickly find yourself chasing down stories and indicators of compromise (IOCs) that aren’t relevant to your needs.
Remember: media stories might be interesting, but they often aren’t relevant to a specific organization.
By contrast, good threat intelligence always has two characteristics:
-
It’s relevant to your organization
-
It’s directly actionable
It might not be exciting enough to get the whole world talking about it, but if actioned, it will help improve your organization’s security profile.
Threat Intelligence-Led Pentesting
So how does threat intelligence relate to pentesting? Simple: It helps testers accurately emulate the activities of real threat actors.
That includes:
-
Targeting your organization’s most at-risk assets, systems, and applications based on the latest threat activity.
-
Applying the most current tactics, techniques, and procedures (TTPs) used in your industry and geographic location.
In other words, threat intelligence-led pentesting helps testers assess an organization’s resilience against simulated real-world events. Since this is exactly what pentesting is intended to do, there is a clear value to incorporating threat intelligence in the pentesting process.
Pentest Threat Profiling
So what does threat intelligence-led pentesting look like in practice? First, the pentester must identify:
-
Which assets are most at risk
-
How those assets are likely to be attacked
With these factors determined, the pentest can be focused accordingly.
At Cobalt, our pentesters use a process we call threat profiling to identify the customer’s most pressing real-world security risks. We use a security questionnaire and our own real-world experience to determine the risk posed by different threats, the specific assets being targeted, and the TTPs most likely to be used.
Our threat profiling process looks like this:
-
Build a picture of the company’s profile and key assets.
-
Define the primary attack surface.
-
Break down key systems into component parts for testing.
-
Identify attack vectors and TTPs for use during testing.
-
Correlate prominent threat actors and objectives.
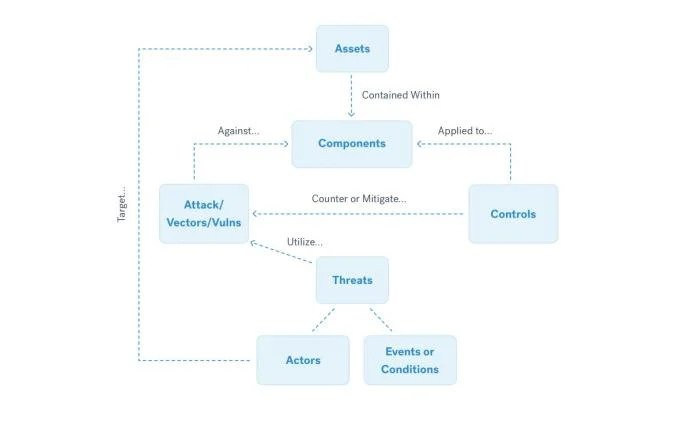
As part of this process, clients with active threat intelligence programs are encouraged to share their findings with our pentesters. This can help to focus pentesting efforts on the organization’s highest-risk assets and threats in order to produce the most realistic results possible.
The Importance of Risk-Based Security
There’s a reason why every major security framework — from PCI DSS to HIPAA to NIST CSF — is based on risk reduction. It’s really the only logical way to build a security program.
Threat-led pentesting is simply an extension of this philosophy. It’s a way to identify an organization’s highest-risk threats and assets so they can be subjected to focused, realistic pentesting.
Our Pentest as a Service platform builds on this philosophy to ensure our customers are fully prepared for real-world threats. To find out how our platform can boost cyber resilience at your organization, arrange a demo today. Explore other intelligence services with OSINT and Digital Risk Assessment.







