Penetration testing simulates cyberattacks against a digital system to discover vulnerabilities ranging from security misconfigurations, poor application design, system glitches and opportunities that attackers can leverage.
Also known as pentesting or ethical hacking, this process helps businesses perceive themselves through the eyes of cyberattackers. Thus, enabling them to discover existing system weaknesses and proactively prevent exploitations.
This becomes critical when considering how frequently cybercrime impacts businesses, reportedly costing an estimated $10.5 trillion annually by 2025. In the words of former IBM CEO Ginni Rommety, “cybercrime is the greatest threat to every company in the world.”
As threats increase, Pentesting as a Service (PtaaS) is fast becoming a reliable method to mitigate them, remediate vulnerabilities, and reduce the risk of a potential breach. Apart from answering “what is penetration testing,” this article explains the fundamental insight into penetration testing stages, processes, and methods.
Penetration Testing Process: Stages of Security Testing
The timeline for a business to commence its penetration testing process depends on several factors: budget, number and size of online assets, compliance or regulatory requirements, customer demands, and the overall IT infrastructure.
After accounting for these factors, the business can follow these six penetration testing stages toward successfully boosting its cybersecurity. To explain this in detail, we’ll use the Cobalt Pentest as a Service (PtaaS) solution:
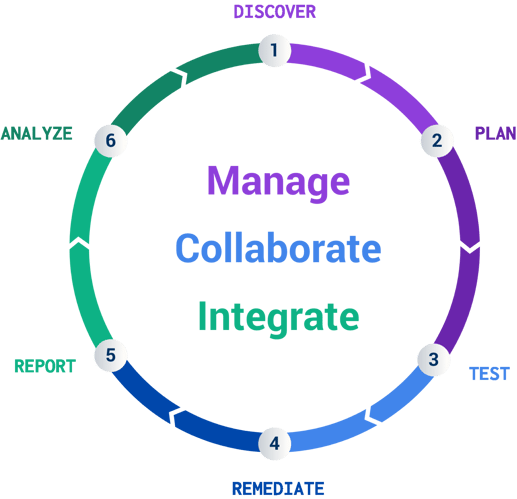
1. Discover
One of the most important penetration testing stages is the discovery phase. This phase helps all parties involved in the test, including your engineering or security teams, Cobalt’s team of expert penetration testers, and other ancillary parties such as stakeholders set up for the test.
The discovery process, as the name implies, involves discovering or mapping the in-scope attack surface. Done in partnership with the Cobalt PenOps Team, this stage will allow for the best assignment of a Cobalt Core Pentester Lead and Domain Experts.
For best results, the pentest team comprises individuals with the skills that align with the required technology stack, experience, and availability. Moreover, the Cobalt platform offers a Slack channel for businesses to use and communicate with the testing team directly and in real time.
Frequent communication between the pentesters and the target business has multiple benefits. First, it’s important because it allows the Cobalt pentesters to gain enough information to help them recognize weaknesses/vulnerabilities more quickly. Frequent communication also empowers developers to ask pentesters questions and increase their security knowledge.
2. Plan
In the planning stage, the business and Cobalt team work together to define the goals and scope of the penetration test. This stage also helps teams get to know one another prior to the test and share critical information such as domain and network names to understand the inner-workings of the test’s target.
This stage often involves communication with the Cobalt team via the platform, Slack, or through a call. Keep in mind that the goal of the planning stage with Cobalt is to give the business an agreeable timeline and completely prepare for testing to start — all the while leveraging the speed a Pentest as a Service platform offers.
3. Test
In the test stage, security experts analyze the target for existing security flaws and vulnerabilities that malicious actors might exploit if not properly fixed. The pentest team collaborates with your development and infosec teams to not only accomplish security testing objectives, but also explain important details or answer questions.
The team reports findings in real time and shares important information — severity level, how to recreate the issue, and how to fix it — directly in Slack and on the Cobalt platform. Businesses have the option to send this information to their developers’ issue trackers through native integrations.
4. Remediate
The remediation stage of the penetration testing process focuses on escalating findings and fixing them. This occurs via an interactive and ongoing process. This stage is the structured approach to triaging fixes and then starting remediation.
A great benefit of the knowledge-sharing available on a PtaaS platform compared to traditional penetration testing is when pentesters can share different attack vectors for remediation teams to consider. For example, when a developer has sent a vulnerability back for a retest. If testers are still able to exploit the vulnerability through multiple avenues and development teams only remediated one, they will go back to you and explain in more detail the other attack vectors.
5. Report
You can find reports in several formats that suit different stakeholders like customers, executive teams, and auditors.
If a comprehensive pentest report is included in the engagement and needed — at the end of the test, the Cobalt Core Lead provides a report. For Agile Pentests, the team will receive an automated report for internal stakeholders.
6. Analyze
The sixth and final stage of the penetration testing process involves thoroughly analyzing the penetration test results. Here, you explore the report with useful data comparing the business’s risk profile against the platform’s benchmark.
This final stage also involves recognizing some prevalent systematic weaknesses to inform development teams and drive the maturity of security programs. Although it is the last stage, it’s undoubtedly one of the most important. If analyzed properly, this will significantly reduce the chances of suffering a breach in the future.
Penetration Testing Methods
Penetration test service providers commonly use three different penetration testing methods to uncover existing vulnerabilities including white, black, and gray-box testing. Here’s what they mean and how they differ:
1. White-Box Penetration Testing Method
With this white-box or clear-box penetration testing method, pentesters have full access to the code. They receive information about the software architecture, source code, and other relevant information.
Here you share the full system and network credentials and network maps with pentesters to save time researching this on their own and thus, increasing time spent on actual testing.
A pentester with such knowledge can also conduct the test in less time, making it one of the fastest types of penetration tests. Moreover, the white-box tests allow for a more thorough penetration testing process compared to other penetration testing methods.
2. Black-Box Penetration Testing Method
Unlike the white-box test, there is no information given to the pentesters to attack with. Instead, the pentester operates like an attacker with no information provided.
In a real-world scenario, a black-box test is similar to how attackers carry out an attack without knowing all the ins and outs of an asset or network, including accessing information to execution and eventual exploitation.
Oftentimes, the lack of information forces the pentester to launch a full-scale attack against the IT infrastructure to find a weakness worth exploiting. The absence of information means the test can take a long time.
More often than not, pentesters will pair manual efforts to breach a system, while also relying on automated processes to fully uncover existing vulnerabilities and weaknesses in a trial and error process.
Experts consider the black-box testing as the most genuine test because it shows how an assailant with zero inside knowledge could compromise a business. On the other hand, it can be one of the most expensive penetration testing methods.
3. Gray-Box Penetration Testing
The gray-box penetration testing method mixes white-box and black-box testing methods. Here the pentester has incomplete information about a specific application’s internal workings. However, they receive some information or privileges such as access to the system architecture diagrams, source code, or select login information.
In a similar fashion to white- and black-box testing, gray-box testing leverages automated and manual testing processes to identify weaknesses. This penetration testing approach allows the pentester to focus their efforts on areas of the systems they have the most knowledge about and then try to exploit any vulnerability.
Despite the pentester having only partial information, there is a high probability of finding the difficult security loopholes when using the gray-box method. Many businesses favor this approach because it offers a fine blend of authenticity and efficiency but also requires more initial setup than a white- or black-box test to clearly define the information shared with pentesters.
Why Penetration Testing is Important?
Now that we understand the penetration testing stages and different types of tests, an important question remains likely with stakeholders paying the security bill — why is penetration testing important?
The rise in cyberattacks in today’s world is a core reason many businesses turn to some form of penetration testing. Industry experts predict the global penetration market size to increase from $1.6B in 2021 to $3B by 2026, with a CAGR of 13.8% in that period.
Ideal times for businesses to consider a penetration test include:
- after upgrades or changes are implemented to their IT infrastructure
- changed end-user policies, or applied security patches
All of which create an ideal time to try a smaller, targeted Agile Pentest compared to a Comprehensive Pentest for compliance.
Here are other reasons penetration testing is important for businesses:
1. Penetration Testing Improves Risk Identification
Risk identification is one of the cornerstones of all penetration testing processes, and coincidentally, it is a common strategy among cyber attackers as well. However, early and frequent penetration tests provide insight into the channels in your applications or networks that are most at risk. This also helps businesses discover the type of security protocols or tools they need to invest in.
2. Vital in Decreasing Prevalent Errors
Sometimes security vulnerabilities exist because human errors occur in development, which attackers can exploit. Pentest reports help developers identify future errors that may prove costly.
Furthemore, the unique collaboration between pentesters and developers offered by a PtaaS platform supercharges this value for businesses compared to traditionally slow and manual penetration testing efforts that end in a static PDF file. Plus, when in-house developers understand how attackers attack a business, they will better understand security, and be better prepared to prevent errors in the future.
3. Helps in the Anticipation and Preparation of Attacks
Another reason penetration testing is important is to help improve overall security practices when trends emerge from the testing data. One example of this could come from how prevalent certain types of vulnerabilities are over time and if there’s any associated trend to help optimize policies.
Did you change your engineering team structure and start to see a certain vulnerability occur more often across different tests? Thus, a series of penetration tests help businesses examine if their security policies are effective.
Think of penetration tests as a fire drill for businesses that must limit risks and prevent attacks before they happen. After a business conducts a penetration test, it should be better prepared to effectively respond to attackers if discovered in their systems.
Conclusion
Penetration testing finds vulnerabilities in systems and software before attackers have a chance to exploit them. It helps boost a business’s security stature while saving money and resources that cyberattacks could cost.
Think your business is due for penetration testing? Cobalt’s Pentest as a Service (PtaaS) has all you need to uncover vulnerabilities to help keep your business functioning optimally.