Each year, we publish The State of Pentesting report to provide a detailed overview of vulnerabilities and identify the trends and hazards that impact the cybersecurity community. We gathered data from over 1,500 pentests performed in 2020 to learn about the assets getting tested and the vulnerabilities discovered, along with interviewing over 600 security practitioners to learn how that data changes across different industries, company sizes, and more.
It’s no secret that cybersecurity is continuously evolving in today’s landscape, and vulnerabilities are a key driver of that change. That being said, here’s a sneak peek into The State of Pentesting 2024.
What are the biggest security vulnerabilities we observe?
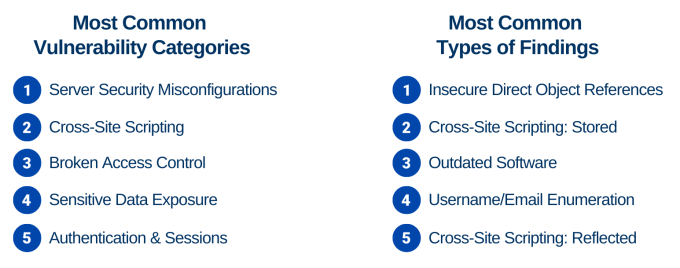
A core change we made for the 2021 report is that our focus is more granular. Rather than come to a halt at vulnerability categories, this year we analyzed individual findings in order to pinpoint the areas where teams are struggling, assess what they can do to remediate, and better yet prevent those vulnerabilities.
What’s the difference between vulnerability categories and types of findings?
Many findings fit into a specific vulnerability category. Vulnerability categories act as an umbrella term that can encompass a variety of more specific findings, each with a different level of risk, impact, or severity. By including both, we’re able to go more in-depth about where exactly companies are struggling.
The latest findings show security teams have been dealing with the same top 5 vulnerabilities for 4 years in a row.
There are several possible reasons for this, including the following:
- Gaps in secure development
- Insufficient investment in security awareness and training
- Ineffective remediation
- Bugs staying open because of low perceived impact and/or lack of resources

These statistics lead us to believe that security teams are struggling to effectively remove and prevent issues that are well known in the industry. By discovering these flaws, Cobalt is able to expose gaps in security and help prioritize remediation efforts with our Pentest as a Service platform.
Why are companies struggling with the same problems year after year?
We took a look at the bigger picture to assess why teams continue to struggle with the same types of problems, testing 4 different theories with 601 security practitioners across the US and DACH area. Download The State of Pentesting 2021 to see the results, along with a detailed list of instructions on fixing and preventing each vulnerability described in the report










