Successful phishing campaigns are one of the most common causes of a cyber breach. In fact, over 80% of reported security incidents are tied to phishing attacks according to CSO .
Whether the attack comes in the form of a targeted campaign against your C-suite or a spray-and-pray campaign, understanding how your controls and users stack up to this attack method is key to preventing it. Cue Cobalt's New Phishing Services. Our seasoned security experts are ready to partner with your team to strengthen your security defenses.
Dangers of Phishing
Through calculated social engineering, attackers are able to compromise sensitive data resulting in damaged brand reputation, loss of customers, and more. Phishing attempts look like they come from a legitimate, trusted source, yet they expose businesses to a variety of risks. With that in mind, trust between an organization and its customers is key and security is at the forefront.
1.5 million new phishing sites arise every month, with more than half of IT decision-makers noting that targeted phishing attacks are their top security threat, according to WebRoot.
The 3 most common types of phishing are:
1. Spear phishing
Spear phishing attacks are personalized to their targets, with the goal in mind to obtain as much sensitive information as possible.
2. Email phishing
Email phishing involves attackers sending fake emails disguised as legitimate financial institutions, government agencies, and more to collect personal information.
3. Whaling
Whaling uses the same techniques as spear phishing, yet this method specifically targets executives in organizations. Executive phishing or whaling often aims to breach a network by leveraging the executive’s power within an organization to gain access.
Although phishing and spear phishing create a window of opportunity for attackers, Cobalt’s phishing services have the right solutions to mitigate risks with the benefits of phishing testing.
Phishing Testing Services
At Cobalt, we work directly with you to understand what you need tested and to build a custom program.
Whether we’re testing your technical controls through a complex campaign or testing your end users, you can trust us to supply you with a detailed report focused on key statistics and concrete remediation guidance. And — the more regularly you test with us, the more insightful your data becomes for the future of your security posture.
Cobalt’s Phishing Testing Process
We first listen to the needs and end goals your organization has in mind and from there, we share our plan of action based on a customized roadmap. Once the phishing engagements are underway, Cobalt team members are available for check-ins through the final stages. After the engagement is complete, Cobalt provides a detailed, anonymized report that includes:
- Specific suggestions from our experts
- Detected areas of weakness
- Recommendations for remediation and areas of improvement
Phishing Email Testing for Employees
Cobalt also offers phishing email testing for employees, where an email is sent out and used as a test run for determining whether an email is legitimate or a potential phishing attempt. With phishing awareness testing, you can gauge the effectiveness of your security awareness training and know the next best steps for training employees on how to spot and handle a phishing attempt before any real loss or damage occurs.
Benefits of Phishing Testing
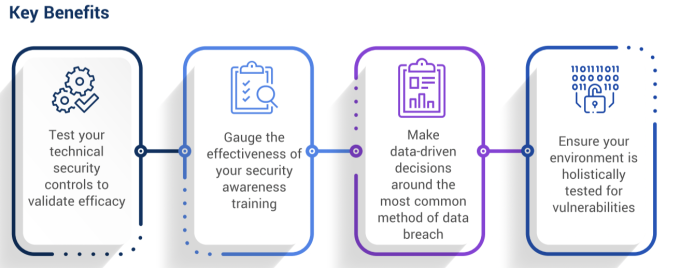
What else can you expect with Cobalt’s Phishing Engagement Services?
Access to Cobalt’s PS Ticketing System
All questions are submitted via email and forwarded to Cobalt’s Cybersecurity Services ticketing system. This allows us to keep track of submissions, response times, and responses.
48 Hour Response Time
Within 48 hours (Monday-Friday) our team will respond to the question, or provide an estimated response time. If a question warrants a call, a consultant will reach out to schedule time.
Best Practice Templates
Cobalt offers templates, or best practice examples, for customers to use as a baseline.
Cobalt’s Cybersecurity Services is your partner beyond the pentest. Learn more about the benefits of phishing services by Cobalt. Explore all of Cobalt’s Cybersecurity Services.








