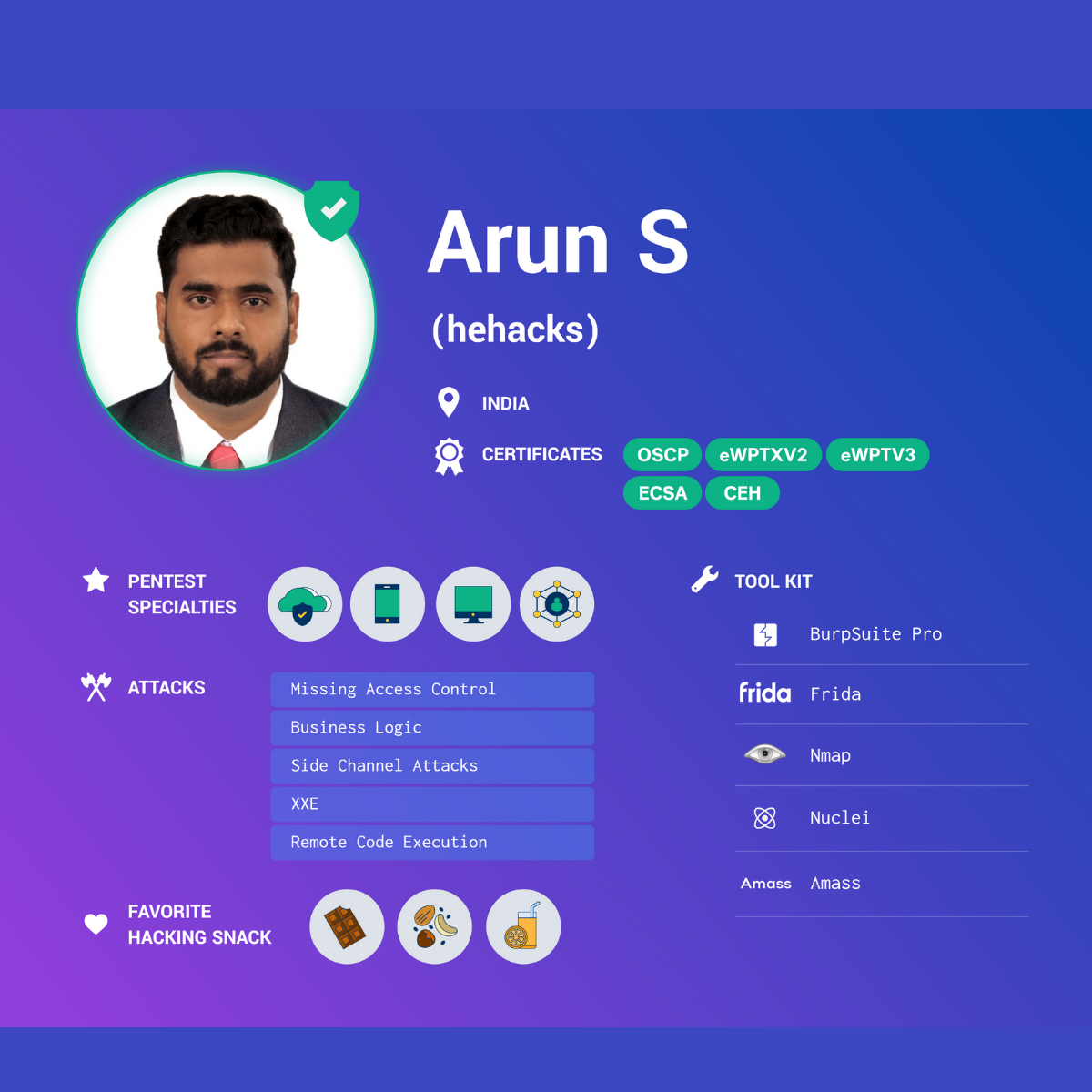
Pentester Origin Story: How did you first get involved in pentesting?
Back in time, when I was in 2nd year of engineering, our college got an invitation from a nearby college that had multiple events organized. One of the events was “Ethical Hacking,” which fascinated me a lot, and without a second thought, I decided to participate.
In this event, the speaker presented two laptops and demonstrated how he gained access to the other laptop from his machine via some graphic representation. I am still unable to figure out how he did that, but this particular demonstration was the turning point of my life, and I decided to dive deep into it. This is how I decided to start my career in cyber security.
After completing my engineering, the journey was rock bottom. It’s not easy for everyone to get a job with a low academic score in engineering. I was one of them. I applied for jobs, attended many walk-in interviews, and got my first job in the networking field as a network engineer. I knew this was not my path, and my mind was still into ethical hacking. I used to work from 9 am to 6 pm (we did not have Saturday and Sunday off), I utilized my post-working hours to study ethical hacking and started researching about it. I still remember when I read the theory and tried to visualize how virtual machines work to set up Kali Linux, and then I started practicing. After learning for all these years, my hard work paid off.
I reported a vulnerability in Microsoft and got into their Hall of Fame list. That’s it. Then the journey of becoming an ethical hacker started. After that, I never looked back. I got many halls of fame in top-notch organizations. During this span of time, I started getting invitations from various top engineering colleges in Mumbai (India) to conduct workshops on Ethical Hacking. I decided to share this knowledge without any monetary reward to help beginners. I have conducted many talks at various colleges, which can be found here. So, with this knowledge, skills, and many HOF, I got my first job in Cyber Security in 2013.
What motivates you when it comes to pentesting?
Always keep learning and never give up attitude. Yes, you read it right …learning motivates me to do much more into pentesting. This field is a big ocean, the more you learn, it is like just taking a bowl of water from the ocean and again and again repeating it. This water is nothing but the knowledge of different attack vectors and new Zero-day exploitation techniques. This all motivates me.
What do you feel makes a good pentest engagement?
Pentest engagement success does not depend on one single aspect, but it’s a combination of
- Defining the exact scope to be covered during the assessment (Scoping)
- Proper walkthrough by discussing the expectations (Scope of Work) from the client before initiating the engagement
- For a pentesting project, teamwork is important
- Communication is critical during the pentesting. During the pentest, give the client regular updates about completed work and insight into the following action plan before the pentest ends. This communication helps the client and tester to update the scope if required.
- Lastly, a detailed report describing the vulnerability details in depth with Proof of Concept (POC) steps so that the developer team can easily understand the vulnerability and fix it.
The collaboration of all the above points makes the pentesting successful.
What kind of targets excites you the most? Do you have a favorite vulnerability type?
I like to explore all kinds of targets like Web Applications, API, Mobile, or Networks but If I want to choose my best target, it will always be “Web Applications” because it's challenging and fun to exploit. Though the application is fully patched, it still has business logic attacks via which you can find interesting vulnerabilities.
Say, you can change any other user’s password and take over the entire account, OR you can view other users’ critical sensitive data, or if a client has implemented a Web Application Firewall (WAF), you can still bypass it. Sounds fun, right? So, the clients, too, love to see this type of issue exposed. Which makes the pentest engagement a win-win for both. This is the only reason I love exploiting web applications as a target, but on the other hand, I love exploring other targets.
Where do you go to learn about different security concepts? Are there specific pages/handles you follow?
I usually follow the Google approach, i.e., if I want to learn about, say, XXE attack and its different ways to exploit, I usually start searching on google and collect all the URLs of various blogs, mind-maps, etc. After collecting all this information, I read and go through it to understand which one is best for me. Later I save those blog URLs and essential notes in my OneNote for windows. This way, after collecting all the information and reading the concept, I store this link in my OneNote for later study and use.
Apart from that, for the learning aspect, I follow PortSwigger Web Security Academy to practice different attacks. To keep myself up to date about new security vulnerabilities reported by my infosec colleagues, I follow publiclyDisclosed on Twitter, and I am very active on Twitter which usually covers all the latest news and updates. You can follow my followers or me to get updates.
How do you conduct research and recon for a pentest?
I will explain this via my favorite target web application testing.
With regards to the particular pentest assigned to me. I first try to understand whether it's falling under the type of black box test or grey box testing. When it's grey box testing, I first go through the documentation to understand the application’s use case, its use, and its purpose. Overall this understanding helps to understand the different attacks which I can pre-plan. I primarily follow a manual testing approach without generating a lot of traffic.
After understanding the application, the next phase is pure recon (pre-auth) testing. First, I conduct the initial recon using various tools, as mentioned below. Looking for any sensitive information which can be accessed without authentication, authentication bypass, etc. Then I try to look for authenticated test cases that cover Stored XSS, SSRF, CSRF, logical / business logic attacks, etc.
What are the go-to tools you leverage?
My go-to tool for the recon process is
For Web Application Testing, my go-to tools are
Burp Suite Professional and its some cool extensions such as
- Error Message Check etc.
For Network Penetration Testing usually, my go-to tools are
Many tools might not be mentioned here, but the above is just a high-level view of the essential tools in my day-to-day engagements.
What advice would you offer to someone interested in getting into pentesting? What do you wish you had known before you started?
Knowing how the network works make jumping into any information security domain easier. Hence, I push if anyone wants to start their career in the information security domain, then first understand the basic networking concept. Hard work and dedication are a must-have but above all, having a mentor in your learning journey is a must. Because he/she will be the one who can guide you, suggest you, and give you a path to reach your goals of becoming a pentester.
Your mentor will be the one who thinks about you without expecting anything in return; he/she will be the one who will always be there for you to lift you up when you fall down hence choosing the right mentor is very important.
For those who are willing to explore the pentesting domains, below are some books I highly recommend to study.
- For Networking Study: Network Security Assessment, 3rd Edition
- For Web Application Security Study: Web Application Hacker's Handbook
What do I wish I had known before I started pentesting?
Well, this wouldn’t have been possible without my mentor's support. In my initial journey, I was lucky enough to have the best mentors, Pralhad Chaskar, Taufiq Ali, and many others. They supported me in the starting phase of the information security journey. Because of their mentorship & support, I already had insights about where I need to reach, what I need to study, areas of improvement, and much more. I am blessed that I have such amazing mentors in my journey. Well, they are still supportive.
What do you wish every company/customer knew before starting a pentest?
I feel every company/customer should know about the overall pentesting workflow. If they know how the pentesting process works, it's easier for them to distribute the pentesting task.
Moreover, suppose the client has prepared detailed documentation of the application feature/functionality or any API documentation and their valid parameter handy. In that case, it's significantly easier for the client to share these details with the pentester team. Also, the client must assign a SPOC (Single Point Of Contact) who knows the entire workflow of the application & the entire network of the organization.
What do you like to do outside of hacking?
I am a self-motivator. Hence outside hacking, I love to write motivational blogs you can find here. I also enjoy traveling & exploring new places.
I am big time foodie (well, I do workout too :P) I have my food blogging YouTube channel, so in my free time, I upload videos of my cooking skill, and sometimes I do vlog as well ^_^ During the COVID lockdown period, I self-learned digital marketing, so I know a bit about SEO (Search Engine Optimization) and overall video editing which I usually do in my free time for my YouTube channel.
Apart from all this, due to my work culture, I need to stay away from my family, so I usually speak with my parents in my free time, and I love spending time with my friends whenever possible.
What are your short-term and long-term goals?
In the context of cyber security, my short-term goal is to enhance my existing skill sets. I believe challenging yourself and continuously learning new things is what makes you shine.
I do not have anything as long-term goals because I always try to challenge myself each day to make sure I learn something new in terms of new attack vectors, WAF bypass techniques, and learning something new with which I am not much familiar. Cybersecurity is a very vast field that covers many domains of cyber security. I am always keen in terms of learning by sharpening my skill sets.