Is my wi-fi connection secure?
You went to a store and wanted to take advantage of the free internet provided by the store, but once you looked, you found two similar wi-fi names. Which one do you think is secure and authentic?
Many stores and shopping centers offer free wifi connections for their customers. How safe are you when you connect to these accessible networks? Are we connected to the free wi-fi connection of the store we visit or are we on a fake network?
While it is very desirable for all of us to use this service, which is offered in almost every store, we should also keep the security aspect in mind. When it comes to wireless network security, it is necessary to make users aware of these attacks by examining an attack scenario we can frequently encounter in real life.
Although there are various network-level attacks hackers perform, for this tutorial, let’s look at some of the most common ones.
Evil Twin & Man In The Middle Attack (MiTM)
A Man-in-the-middle attack (MITM) is listening and changing the traffic passing between a network's target and network elements (server, switch, router, or modem).
Since MITM Attacks are carried out in Layer 2 (Data link layer) in the OSI Model, the attacker can dominate all traffic after a successful attack. This dominance is limitless, from encrypted “https” traffic to unencrypted traffic. The actions the attacker can perform after a successful MITM attack are entirely up to their knowledge and skill set.
An evil Twin attack is a type of MiTM attack in which a hacker performs with a fake Wi-Fi network access point to steal your credentials. It is carried out by simulating the wi-fi connection of the store by the attacker.
The attacker can create the hotspot with the same name as Wi-Fi in a straightforward way. The only thing to do for the attacker who makes his own Wi-Fi network is to wait for someone to join this network. This network created by the attacker broadcasts the same way as the store’s name.
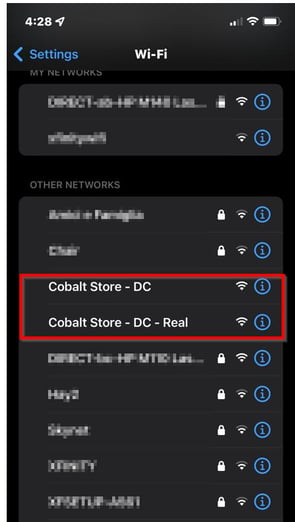
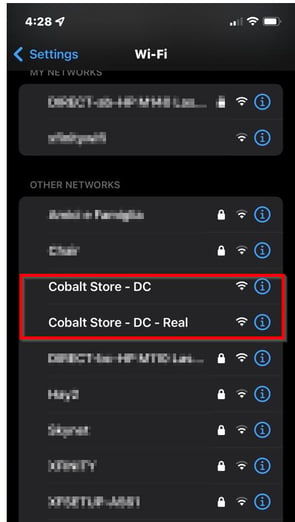
For example, you went to the “Cobalt Store” and realized that your mobile internet connection provided by the GSM service provider was not working. You wanted to use the free internet offered by the store. When you checked Wi-Fi from your mobile phone, you saw two access points, as shown below.
Usually, stores try to ensure their security by creating a captive portal and following up on any illegal situation that may interfere with their customers and their own IP addresses. Therefore, whenever you connect to this free Wi-Fi provided by the store, you are asked to enter some of your information here. With these and similar pages imitated by attackers, attackers can steal your identity information and capture your bank information. Frankly, everything an attacker can do depends on their imagination.
How does it work?
This example is aimed to learn the wireless network password exploitation using the evil-twin attack with `airgeddon` tool.
After the handshake is caught in wifi attacks, the password can only be cracked if it is in the wordlist of the attacker, while the password required by the victim to connect to the network is directly in the hands of the attacker (thanks to the fake captive portal).
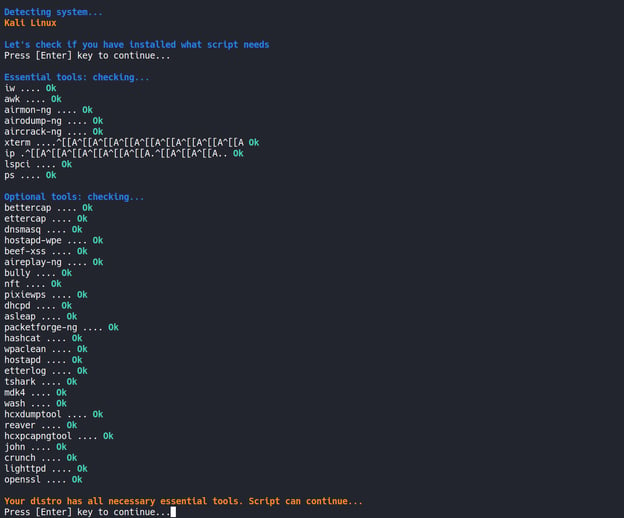
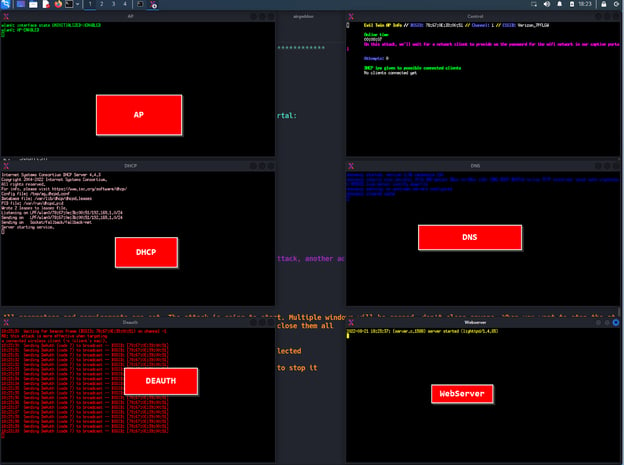
In the image below, we are running the airgeddon tool. We start the tool by checking the installations of all necessary tools by airgeddon.
Once done, the interfaces detected by the tool are listed.
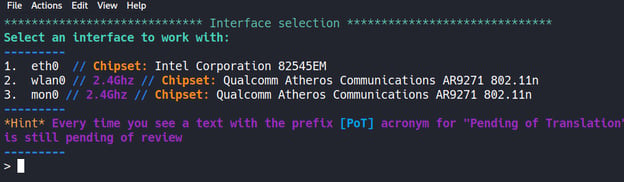
We choose the wireless network adapter in monitor mode, which is necessary for the evil twin attack. (Option #3 in this example). Then, the menu of the attacks we can perform using the tool welcomes us.
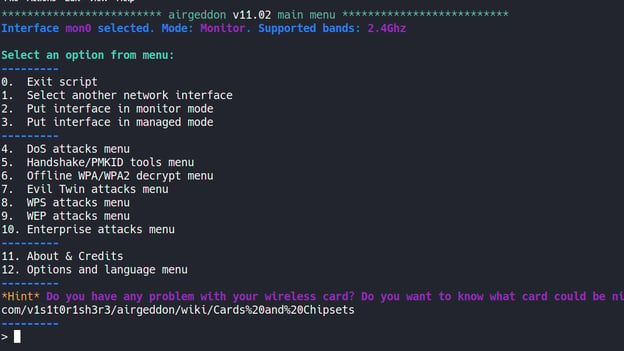
With option number 7, we reach the menu of the "Evil Twin" attacks.
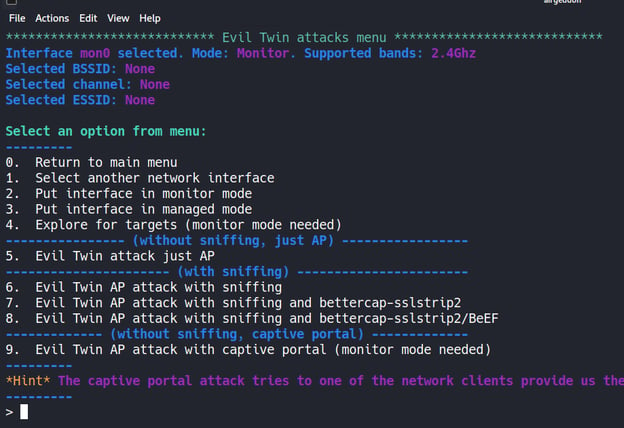
In this menu, there are options where we can create a fake captive portal along with the features we can sniff. By choosing option 9, we can proceed to make a fake captive portal.
The tool then detects wireless network connections by using `airmon-ng`.
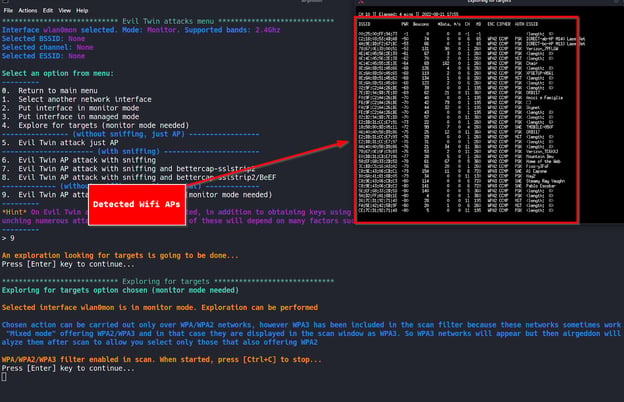
Select the desired connection for the Evil-Twin attack from the detected wireless network connections. In this example, we will choose the “Verizon_7PFLGW” AP.
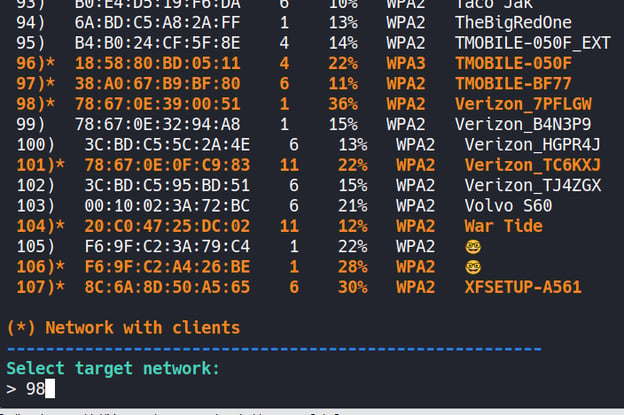
We will try an "aireplay attack" for this wireless network connection.
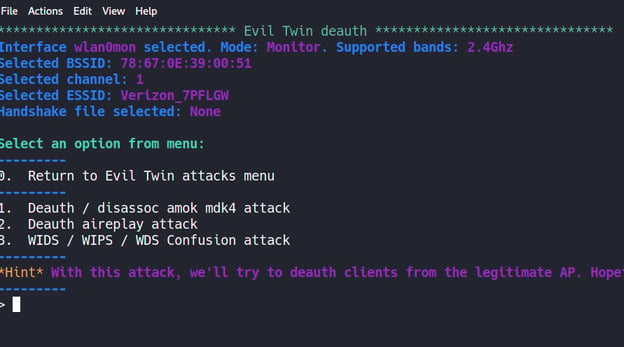
The tool sends deauth packets for STAs connected to the targeted wireless network, allowing anyone to drop from the network. This is known as Deauthentication Attack.
The disconnected STA automatically reconnected to the SSID whose password was already known, providing authentication.
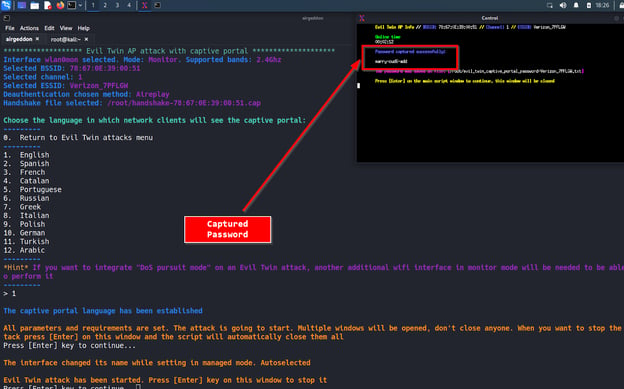
At this stage, airgeddon used the “airmon-ng” infrastructure to capture the authenticated handshake. If we want, we can try to crack the password after this step. However, to crack the password, a valid password must be present in the wordlist that they will use to crack the password.
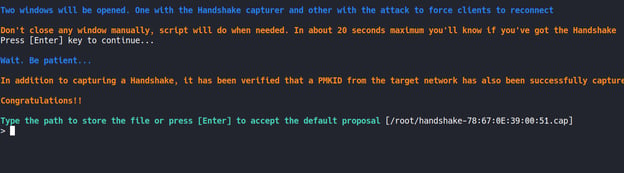
The next step is a fake captive portal. With this captive portal, we can learn the actual password from people who create a phishing page and aim to go to the internet through our fake connection.
In the next step, the tool asks us to choose the language for the fake captive portal.
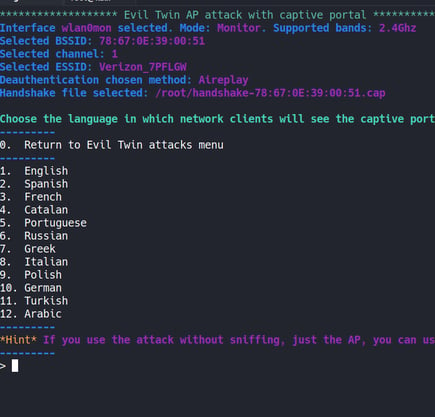
We continue by choosing the English language.
The tool created a rouge access point with the same name as the targeted wireless network connection, DHCP, and DNS server was raised. It will now be able to respond to HTTP requests of victims attempting to join the fake connection and provide them with an IP address.
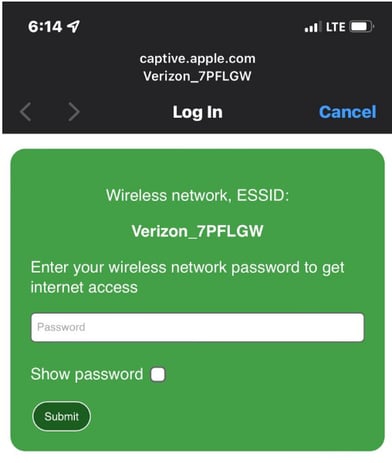
The fake captive portal is presented to users who connect to the fake network. If the users are not very careful, they might enter sensitive details on the fake portal.
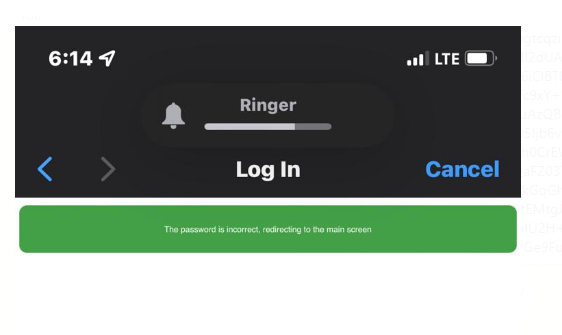
If the user enters the wireless network connection incorrectly, the tool does not allow the internet connection and says the password is incorrect.
So how does the tool know the real password? Of course, by the handshake packages that the attacker captured from the traffic initially.
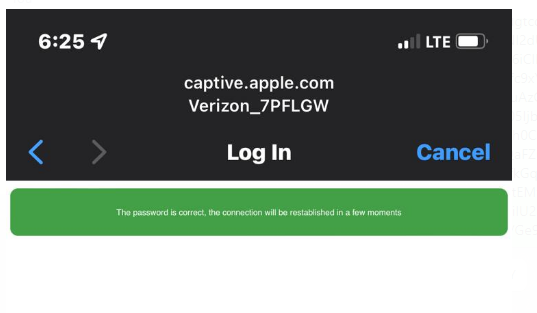
The tool continues to attack until the user enters the real password. The tool completes the attack when the handshake packet is cracked with the real password.
If you try to log in to your bank within a fake wireless network that belongs to the attacker, you may very likely have lost your account details to them.
How to detect & prevent such attacks?
There is no easy way to detect and catch a fake wireless network.
If you do not want your customers to encounter such scenarios, you must take different authentication measures or use WIPS on your captive portal page.
You should also warn your customers against the following situations;
- Pay attention to the wireless network connection names,
- Accessing sites with only HTTPS traffic,
- Cleartext protocols can listen to traffic
- Disabling the auto connect option
- Avoiding personal and important transactions on free internet connections
Illegal internet activities on public wifi networks
Do you know that stores have responsibilities as much as end users in terms of wifi?
You are trying to provide free internet to your customers, but are you sure that you can protect your wireless network connection from people trying to access illegal sites using it illegally?
Do not forget that your traffic can be hidden by different methods, such as DNS tunneling, bypassing the captive portal, and joining the TOR network.
You should have your wireless network infrastructure pentested regularly. Cobalt offers a faster, smarter, and stronger pentesting solution. Book a demo today to see how our network of experienced pentesters can help you stay compliant and secure.