If we could only say one thing to program owners it would be to communicate with your researchers through the comments and evaluation fields. Make them understand why you are doing something and when. This will encourage the best responses, feedback, and retention of talent on your program.
With that in the back of your mind, please also consider the following best practices:
What to Do Initially When You Receive a Report
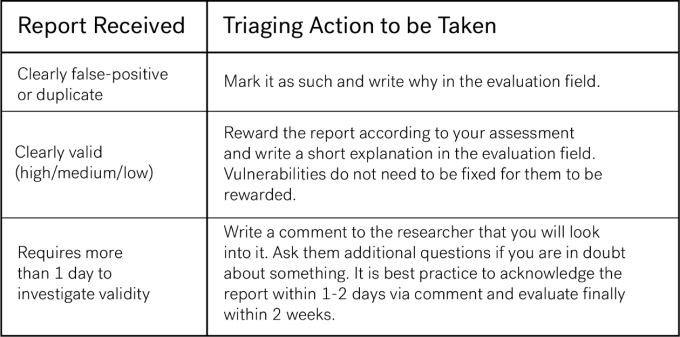
Perform your triaging (reproduce the Proof Of Concept) and do the following based on your findings:
Evaluation and Criticality
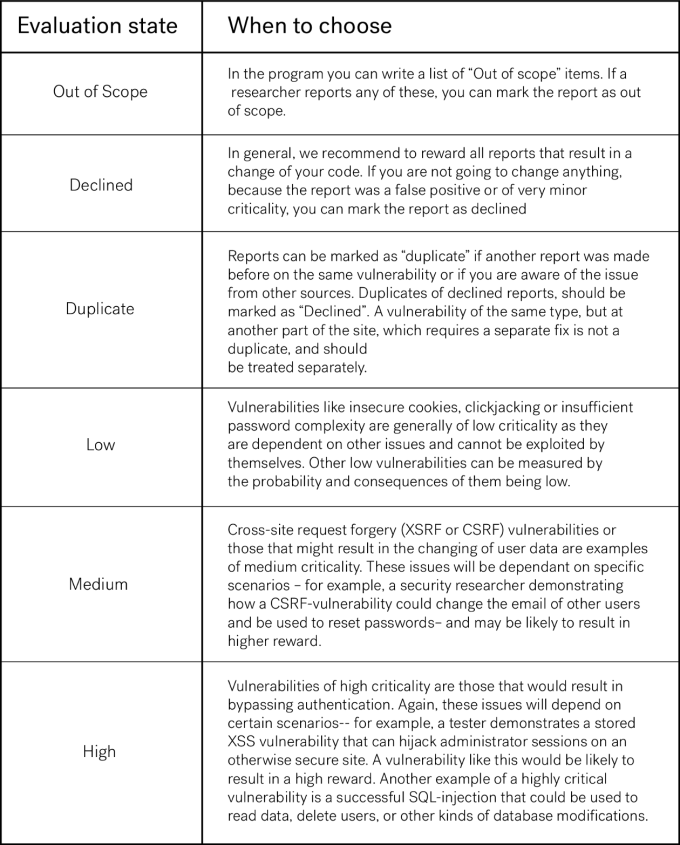
When evaluating reports, how are the various categories defined? Here’s a brief guide:
In addition to the evaluation we always recommend giving written feedback — this is the best to show appreciation and engagement towards the researcher community.
After Evaluation
To keep track of whether a rewarded report has been fixed or not we recommend to use our labelling system and/or our integrations with Github or Jira.
When a report has been fixed it is good practice to write a comment to the researcher telling them so — that way they can check to see if it is in fact patched. It is up to you if you want to reward this extra check by the researcher via our tipping feature.
Disclosure
When a report has been evaluated the business (and the researcher) will have possibility to publicly disclose it. Disclosing a vulnerability report, once patched, is a great way to share security knowledge, acknowledge the researcher’s work and show the world you’re being pro-active about your security.
Happy Evaluating!