This post was updated in 2023.
Fintech cyberattacks impact more than just money, such as breaching required compliance standards or eroding trust with customers.
Further, fintech services have an obligation to protect their customers' data, in addition to their money. At the same time, attackers frequently target financial technology companies due to their motivation for financial gain.
So, what can fintech companies do to prevent the next cyberattack from impacting their business? Let’s take a closer look to understand the importance of a proactive cybersecurity approach.
Importance of Financial Cybersecurity
To further showcase the importance of financial cybersecurity, an IBM research report notes that financial service providers are the most targeted by criminals for the last three consecutive years.
While fintech firms do not have to adhere to as rigorous regulations as their legacy banking counterparts, they still must take their security seriously. Proactive cybersecurity services such as pentesting offer fintech businesses one possible avenue to decrease their risk in the digital world.
Furthermore, the FinTech industry is a common target for attackers. The industry attracts cybercriminals that seek to infiltrate systems to extract sensitive data in hopes to steal credit card information or other financial data for malicious purposes. Attacks on this sector include other vectors such as identity theft, phishing attempts, malware infection, or ransomware.
These should provide companies ample reason to have a strong risk management policy in place. Let’s take a closer look at a few of the core benefits of fintech cybersecurity.
Compliance
Application security will often start with compliance requirements. Followed quickly by the importance of reducing cybersecurity risk.
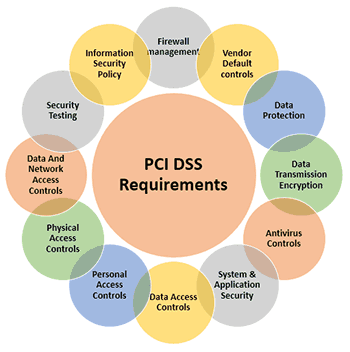
While many common compliance frameworks come to mind, such as GDPR or PCI DSS, financial service providers must follow more stringent regulatory requirements than other industries. For example, PCI DSS requires financial institutions to implement an intrusion detection system to prevent breaches from spreading or going undetected.
With the added compliance requirements for financial service providers, it makes sense to consider a cybersecurity plan to protect your business accordingly.
Fintech Data Protection
While PCI DSS focuses on data protection, it isn’t the only compliance framework or law regulating the topic.
For example, the Gramm-Leach-Bliley Act (GLBA) of 1999 requires specific data security standards for financial information. While these higher standards bring peace of mind and increased protection against consumer data breaches, they also require businesses handling this type of data to invest more resources into security.
With the vast amount of sensitive data stored on a fintech application, it’s critical to secure these systems from cybercrime. Firewalls and other security best practices should be deployed to help secure sensitive information.
Reputation
Lastly, financial institutions have an obligation to their reputation. Few things jeopardize a brand’s reputation than a cyberattack where a customer’s data or financial assets become jeopardized.
Further to this point, financial service providers must establish and maintain trust with their customers. A core component to this rests upon the security of customer’s data and money.
To this point, companies should consider implementing pentesting directly into their software development lifecycles. Thus, aiming for a SSDLC lifecycle for the necessary security to be implemented into fintech apps and other development projects.
Benefits of Using a Fintech Security Company
While internal security teams play an important part for many fintech providers, leveraging the expertise of an external testing team brings many benefits. For example, with cybersecurity constantly evolving, new insights can enhance your internal team with tips shared by external experts.
Furthermore, many growing companies benefit from the increased scalability external information security teams offer.
Augmenting your internal staff with a scalable solution for testing becomes invaluable to both enterprises and rapidly growing companies. For example, as more companies transition to cloud computing, an external team allows companies to do so securely and more efficiently.
Finally, centralized operations for pentesting empower teams to increase their efficiency. Legacy pentest data can be reviewed to find opportunities for optimization to existing workflows and processes. While the centralized data comes with its own vulnerabilities, working with a trusted partner to provide this platform alleviates this concern - especially when the pentest platform provider has gone through the proper compliance frameworks and implemented necessary security protocols.
Pentesting for Fintech Companies
If your fintech company needs a reliable cybersecurity partner for security solutions, trust Cobalt. Cobalt’s industry-leading Pentest as a Service (PtaaS) platform not only unlocks penetration testing at scale but also offers firms for pentesting for compliance - all of which aim to improve your security posture.
Pentesting is a best practice for many different industries beyond fintech. Cobalt also offers a full range of Professional Services for Cybersecurity to help mitigate risk. We help companies ranging in size as well from startups to enterprises and ensure their ecosystems have the necessary security policies and measures.
Explore how data breaches impact different industries to see how pentesting and other security measures help to mitigate against malicious data breaches. Protect your FinTech solution against cybersecurity threats today!